The latest Cloud Security Report by Latio Tech (James Berthoty) is out, and let me just say: it’s packed. If you care about runtime, CNAPP, or the evolving role of AI in cloud security, this one’s worth the read.
But let’s start with the fun part. Sweet Security was recognized as a Cloud Security Leader Leader and a Cloud Application Detection & Response (CADR) Leader. Not one, but two badges. It's always a nice feeling to see the hard work recognized, and more importantly, to see CADR get serious attention.
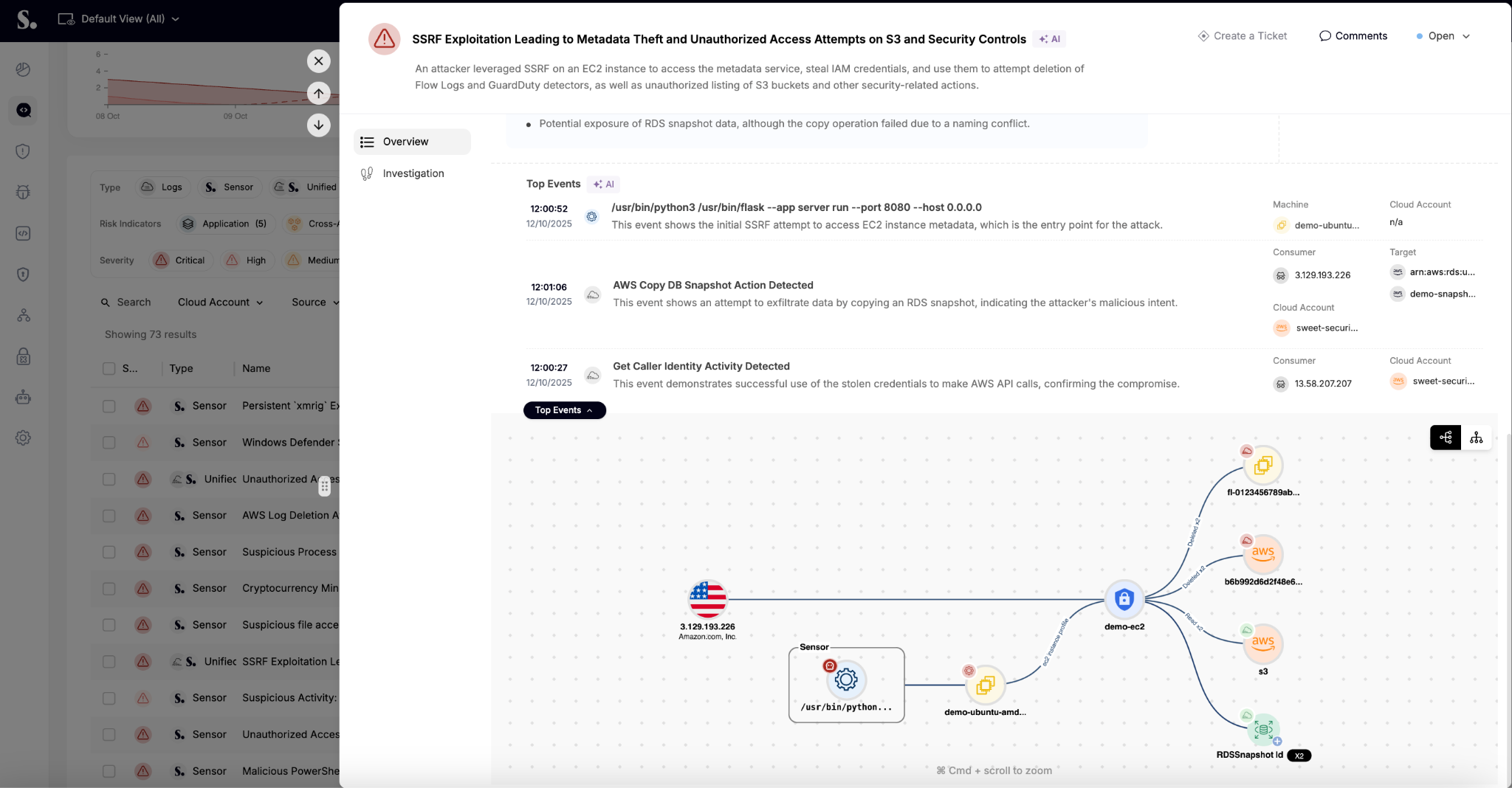
James’ breakdown of Sweet hits on a few things we care deeply about. He describes us as “all about discovering actionable findings” in the cloud. That’s exactly it. From day one, our mission has been to move beyond alerts and give security teams real insight, in real time, based on what’s actually happening in their environments.
That’s where our runtime-powered engine comes in. Whether it's suspicious application behavior, identity misuse, vulnerable secrets being executed, or strange API calls leaving your environment—we’re not just logging it. We’re turning it into an attack story.
And not just one layer. We stitch the narrative across the full stack: from the application, to the container it ran in, to the network traffic it generated, to the infrastructure it tried to exploit. The result is a clear, actionable picture of the incident that teams can respond to immediately.
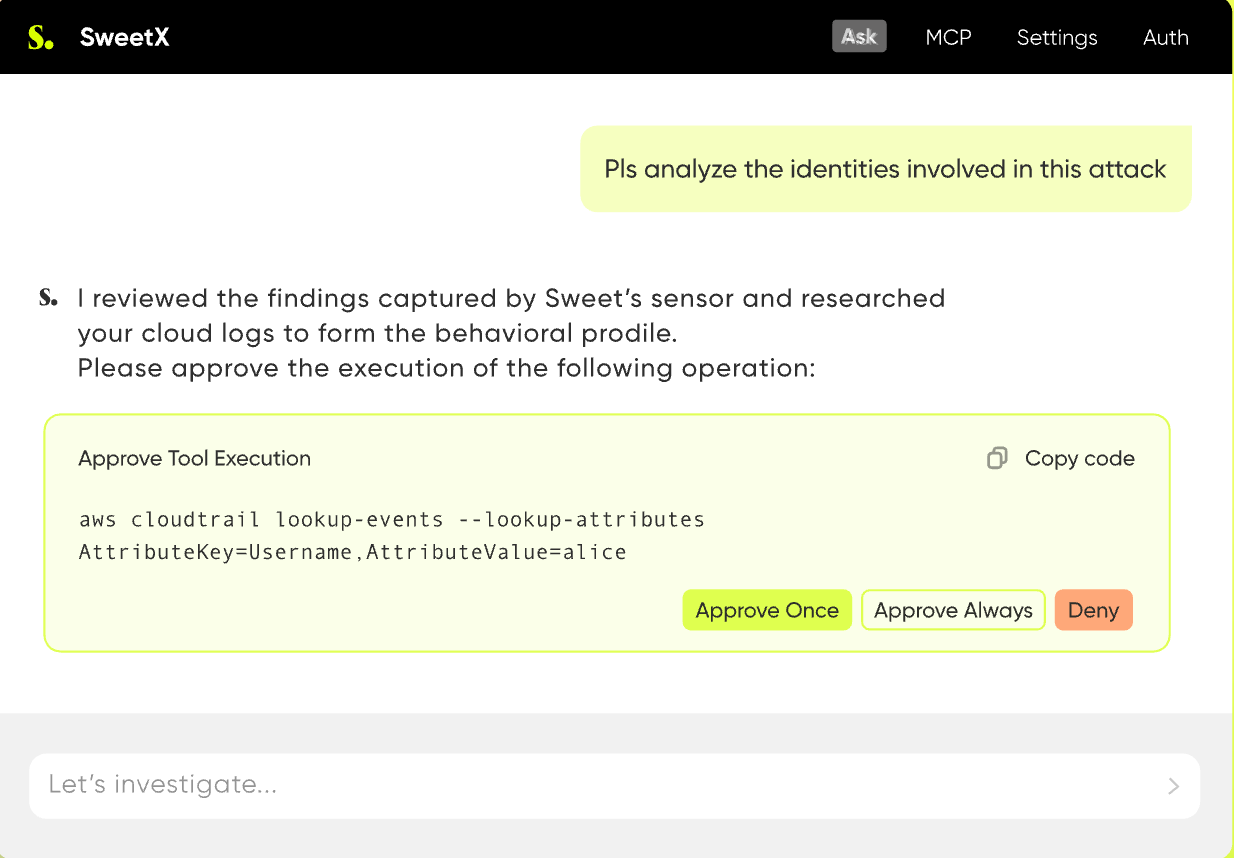
James also gave a shoutout to our AI detection capabilities, like ‘SweetX’, our agentic investigator. ‘SweetX’ takes in thousands of signals from cloud environments and infers root cause in seconds. What used to take hours of manual analysis, now happens in moments. That’s the kind of shift security teams need right now.
And yes, our expansion into the API layer, identity mapping, misconfiguration detection, and secrets prioritization is all built on the same principle: what’s actually running is what matters. Runtime is the ground truth. It's how we reduce noise, reduce blind spots, and help teams act with clarity.
Specialization vs. Consolidation
The report also touched on an ongoing industry debate: Is it better to go deep on a specific part of security, or consolidate everything into one platform?
Honestly, we understand both sides. There’s real value in specialization, especially when you’re solving a problem as complex as runtime protection. You have to go deep. But we also know security teams are tired of juggling a dozen tools that don’t talk to each other. They want visibility across everything. A single source of truth. They want to understand posture and risk and respond to incidents—all in one place.
We believe it doesn’t have to be either-or. That’s why Sweet gives you broad coverage across cloud infrastructure, workloads, and applications, while still being laser-focused on runtime. We consolidate the view, not the mission. You can still bring your favorite ASPM or SIEM—we’ll plug in and make everything smarter.
What’s becoming clear is that the future of cloud security isn’t just about visibility, it’s about context. The best solutions are merging vulnerabilities, misconfigurations, and runtime behaviors into a single asset view, helping teams understand which risks actually matter. That’s exactly what Sweet does—by fusing runtime context with posture data to prioritize the issues that can truly impact your environment.
And while we’re built cloud-first, we also recognize the growing need for hybrid visibility. As more organizations blend cloud-native and on-prem workloads, our runtime coverage extends to Windows and multi-cloud environments, helping teams keep a unified operational picture no matter where their workloads live.
AI Is Joining the Picture. For Real This Time.
AI in security isn’t new. But for a long time, it was mostly just a buzzword or an analytics filter. That’s changing.
This report makes it clear: the vendors getting ahead are the ones treating AI as a core engine, not a bolt-on. At Sweet, AI isn’t just powering detections. It’s deciding what needs to be prioritized. It’s building full incident timelines. It’s giving response teams instructions they can act on immediately. That’s what we mean when we say AI-native cloud security.
AI that interprets runtime signals, maps them back to the originating asset or developer, and helps both SOC and DevSecOps teams fix the issue faster. Runtime alerts go to security operations, posture alerts go directly to developer workflows. It’s one connected loop that makes everyone more effective.
Runtime Is No Longer Niche
We’ve been talking about runtime for a while now. At first, it felt like we were explaining the basics. Now, the industry is catching on—and this report is more proof. Runtime is the only place where you can see how real-world attacks unfold. It’s where you can correlate posture, behavior, and activity. It’s where cloud security becomes cloud defense.
Whether you’re calling it Runtime CNAPP, CNADR, or CADR, what matters is this: security teams want real-time answers and context that crosses layers. That’s what runtime delivers.
We’re grateful to James for the recognition. And we’re excited to keep pushing the boundaries of what cloud security should be.
If you haven’t read the report yet, feel free to check it out here.











