Sweet empowers CISOs to make strategic security decisions, backed by runtime intelligence, automation, and context.

Don't let security decelerate time to market. Sweet shows you where your security efforts needs to be.





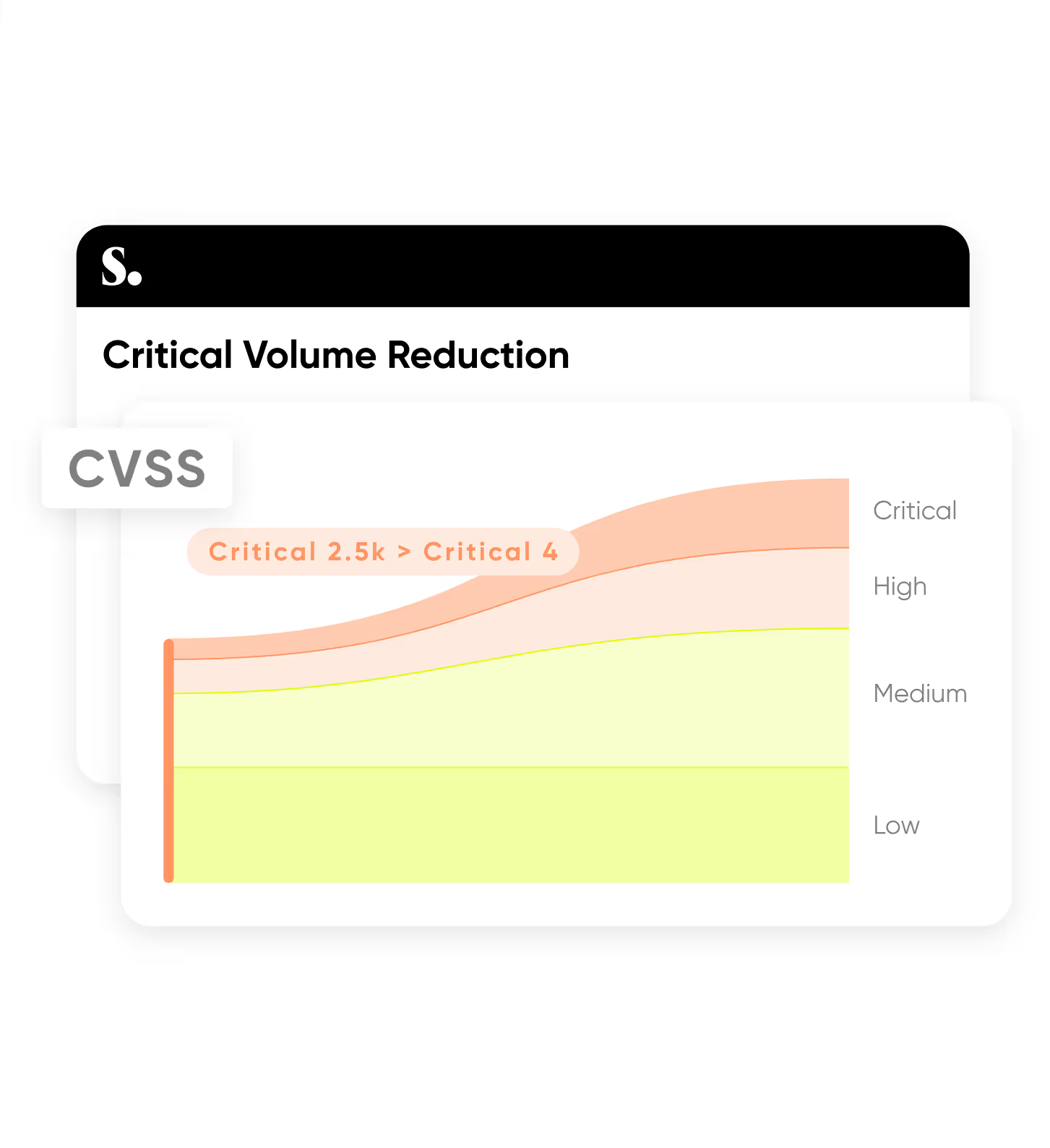
Not all vulnerabilities are equal. Sweet helps CISOs cut through the noise by showcasing what’s actually exploitable — and business critical.
Time-to-respond defines your resilience. Sweet reduces Mean Time to Respond (MTTR) by giving your teams clarity, not confusion.
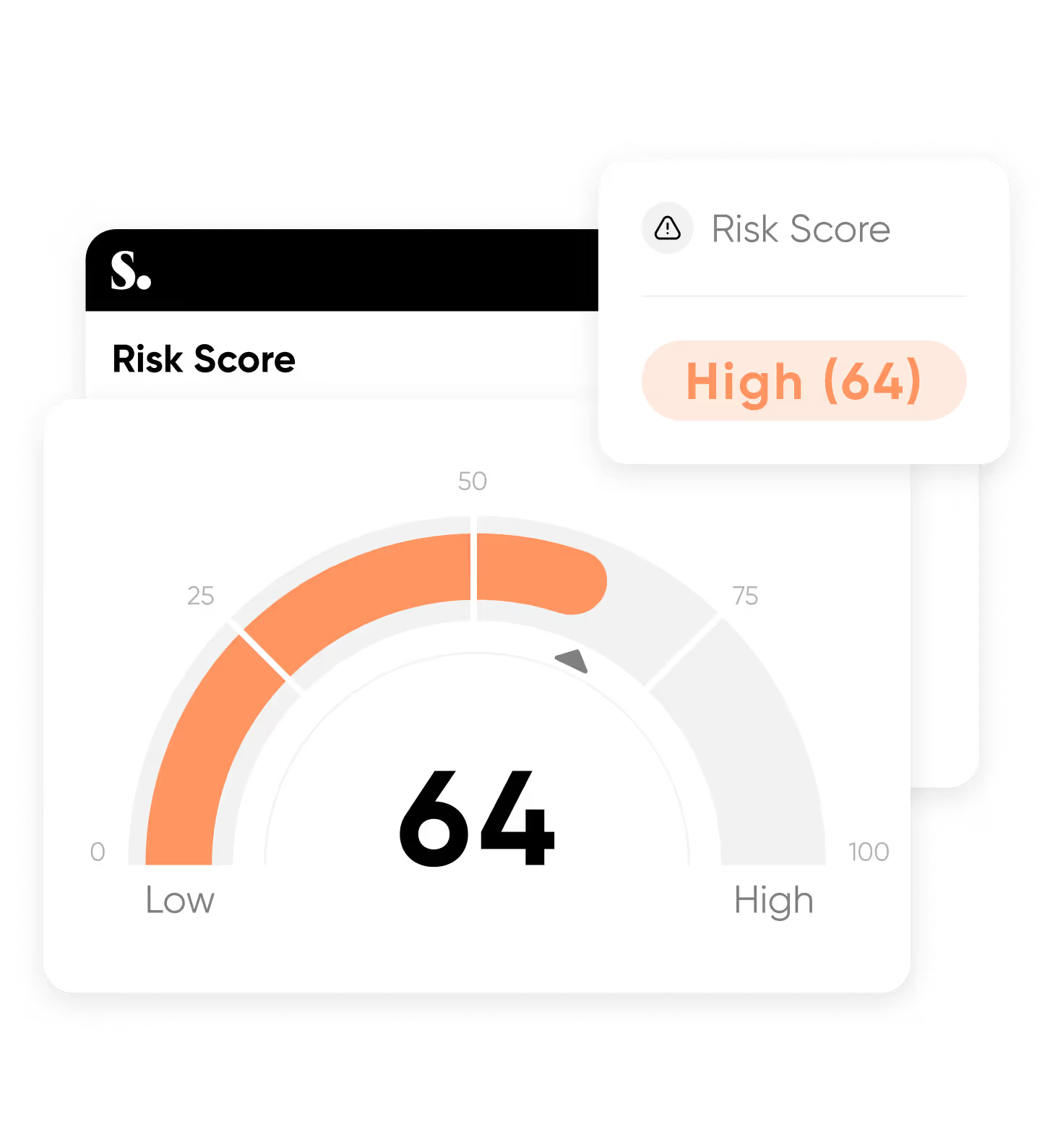
Sweet helps you answer the board’s toughest question: “Is our risk posture improving?”
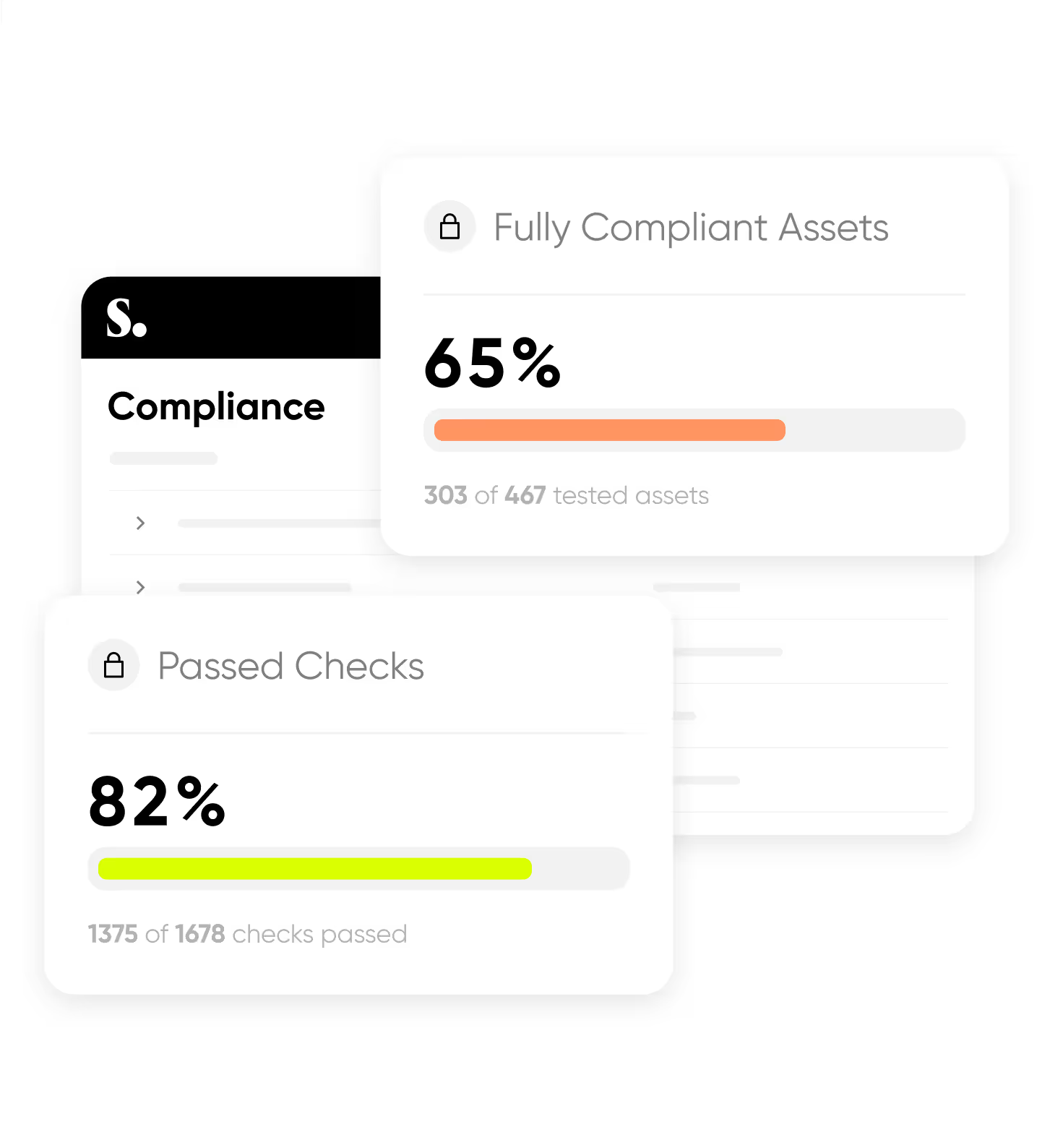
With runtime visibility and automated controls, compliance becomes less about checkboxes and more about real assurance. Whether it’s for your auditor or your executive team, Sweet makes it easy to:






Sweet explains how small security signals become real attacks:
From IAM role misuse to data exfiltration
From vulnerable workload to active C2 connection
From misconfigured API to real exploitation in production
You get explainable security that’s fast enough for incident response and clear enough for board reporting.