

Cut MTTR to 5 minutes with layers-wide runtime context. Sweet is your ADR, CDR, and CWPP combined.

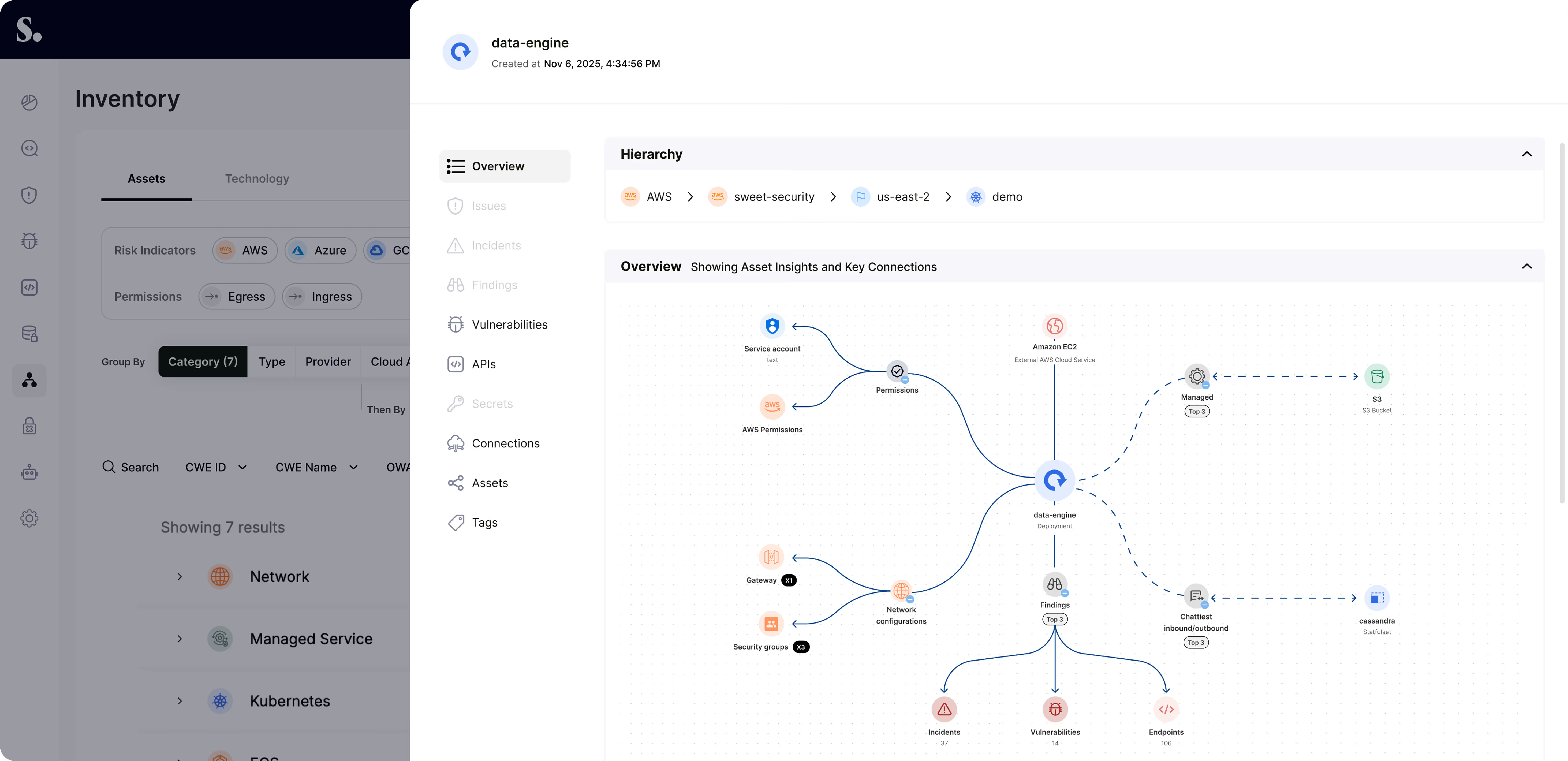
Get full cloud visibility and all the insights you need, in-real time. No more cloud blindspots.

Attain deep cloud protection without performance penalties, through Sweet’s eBPF-based sensor. Protect your cloud at unparalleled speed.
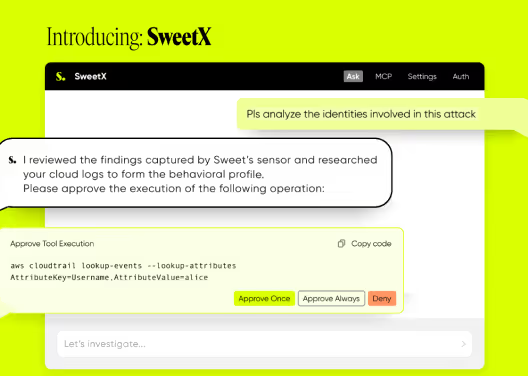
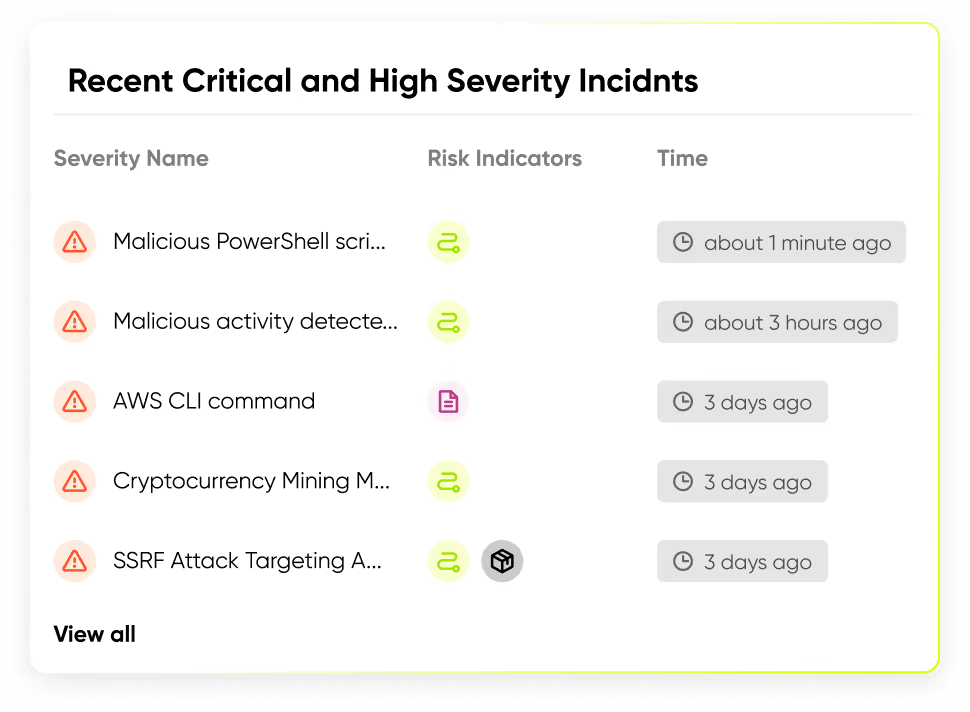
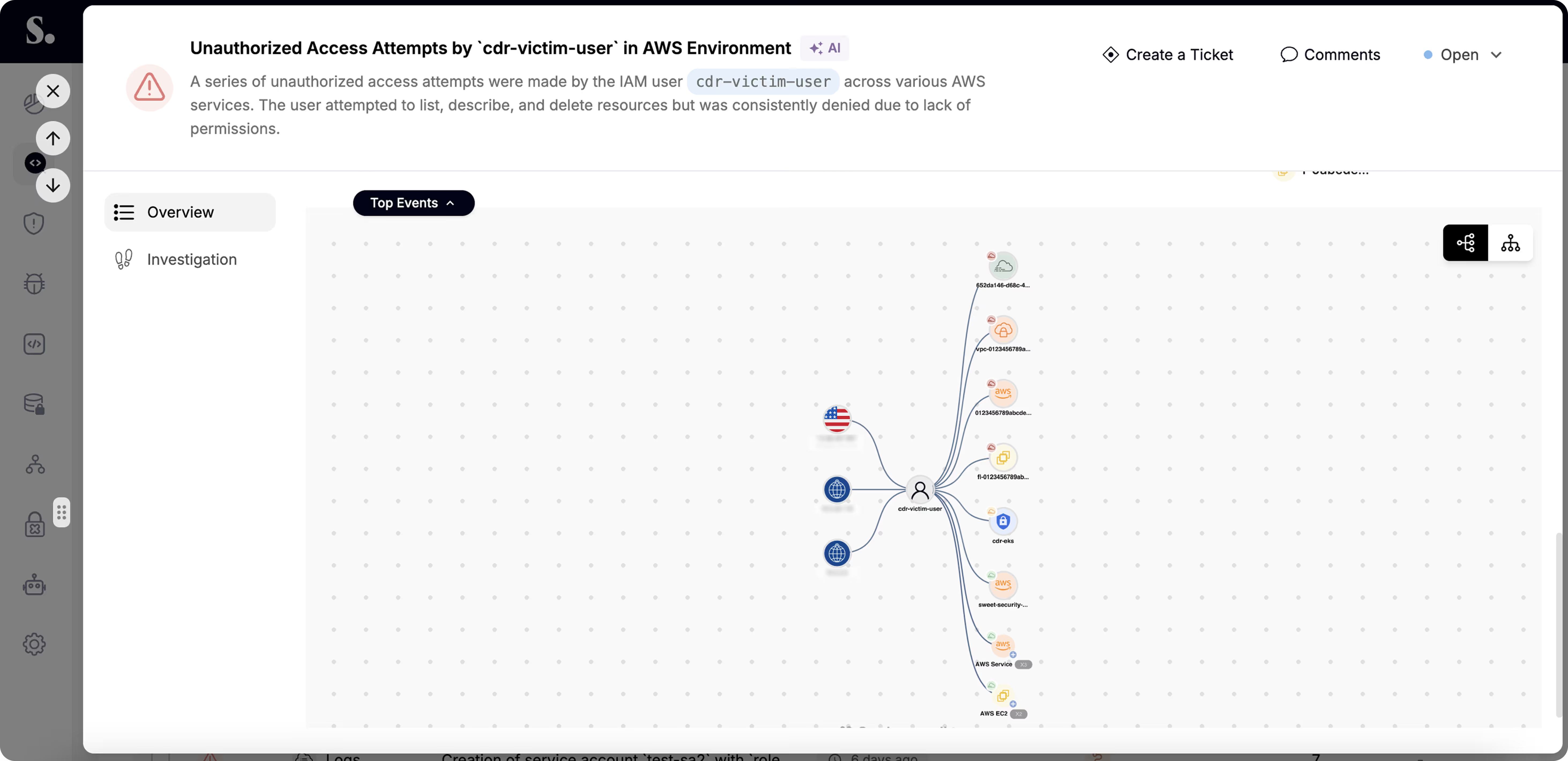
Detect, investigate, and resolve cloud attacks in real time with Sweet’s Cloud Detection and Response (CDR).

Identify suspicious activities involving secrets and identities through anomaly detection, compromise indicators, and behavioral analytics.
See and stop live application-layer (Layer 7) attacks as they happen.
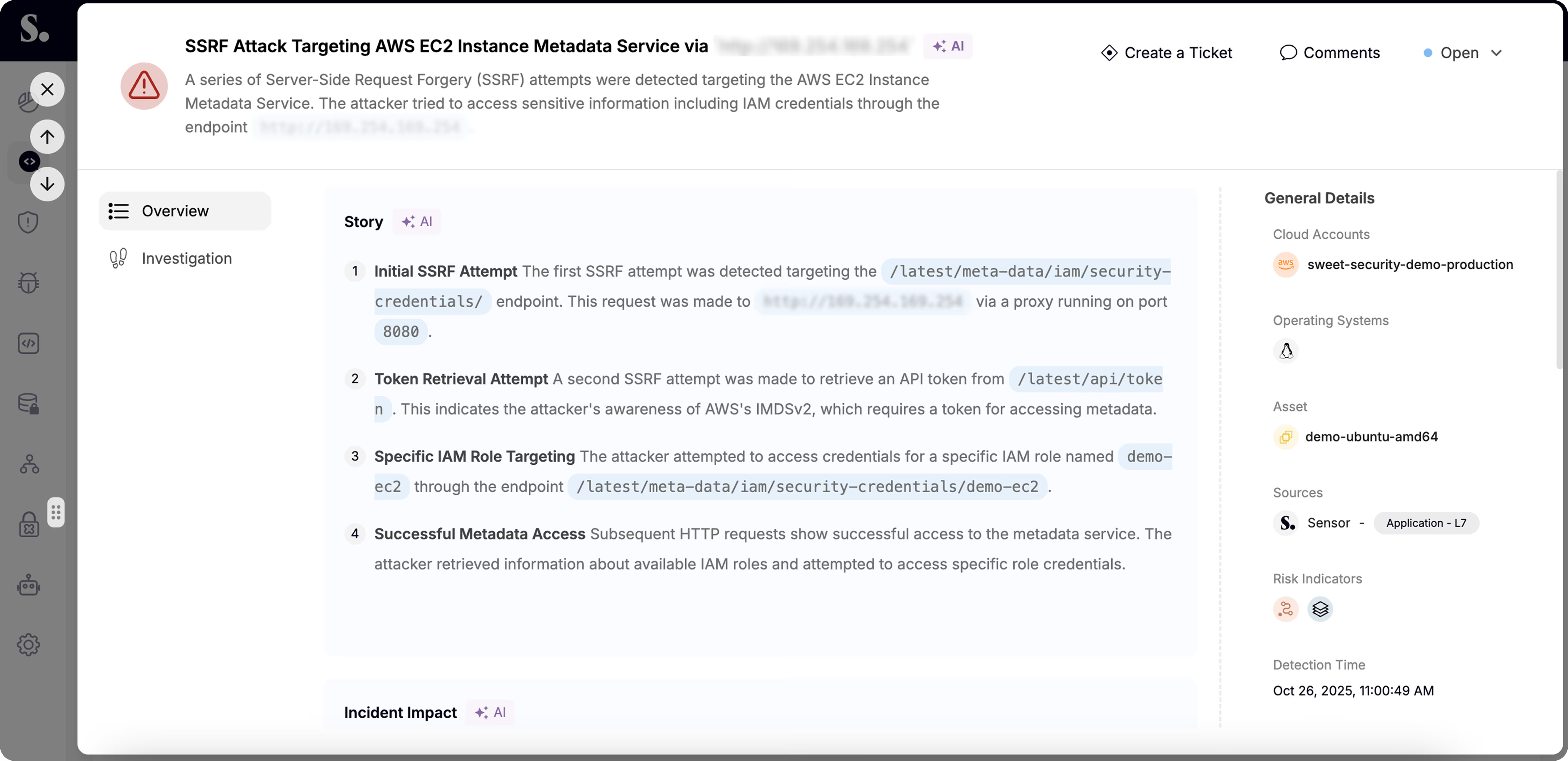
Comprehensive visibility and threat detection across your cloud, workload, and applications.

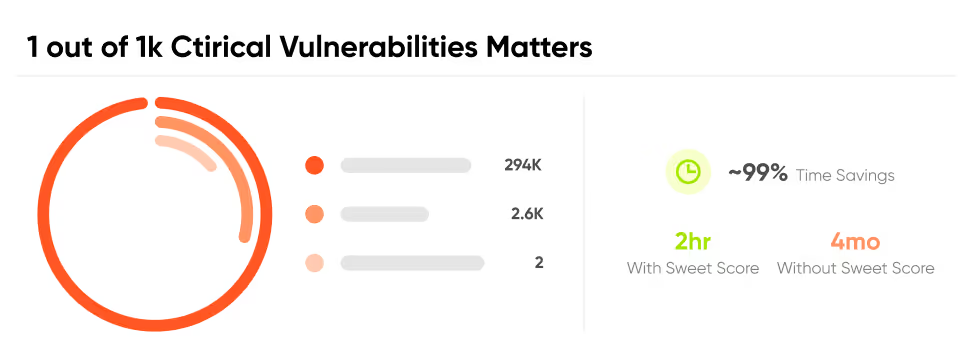
Focus on critical and active risks with runtime-powered vulnerability management.
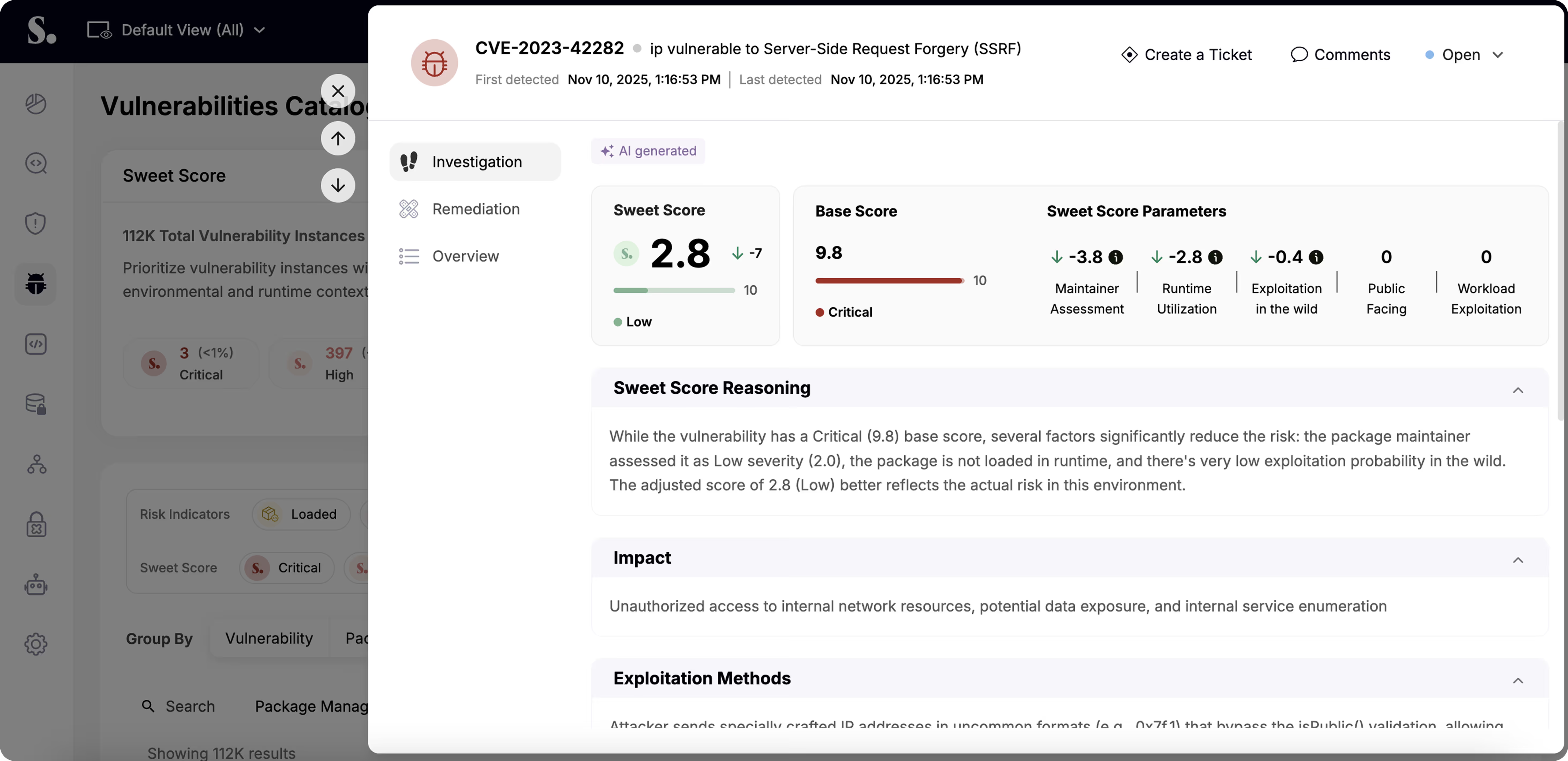
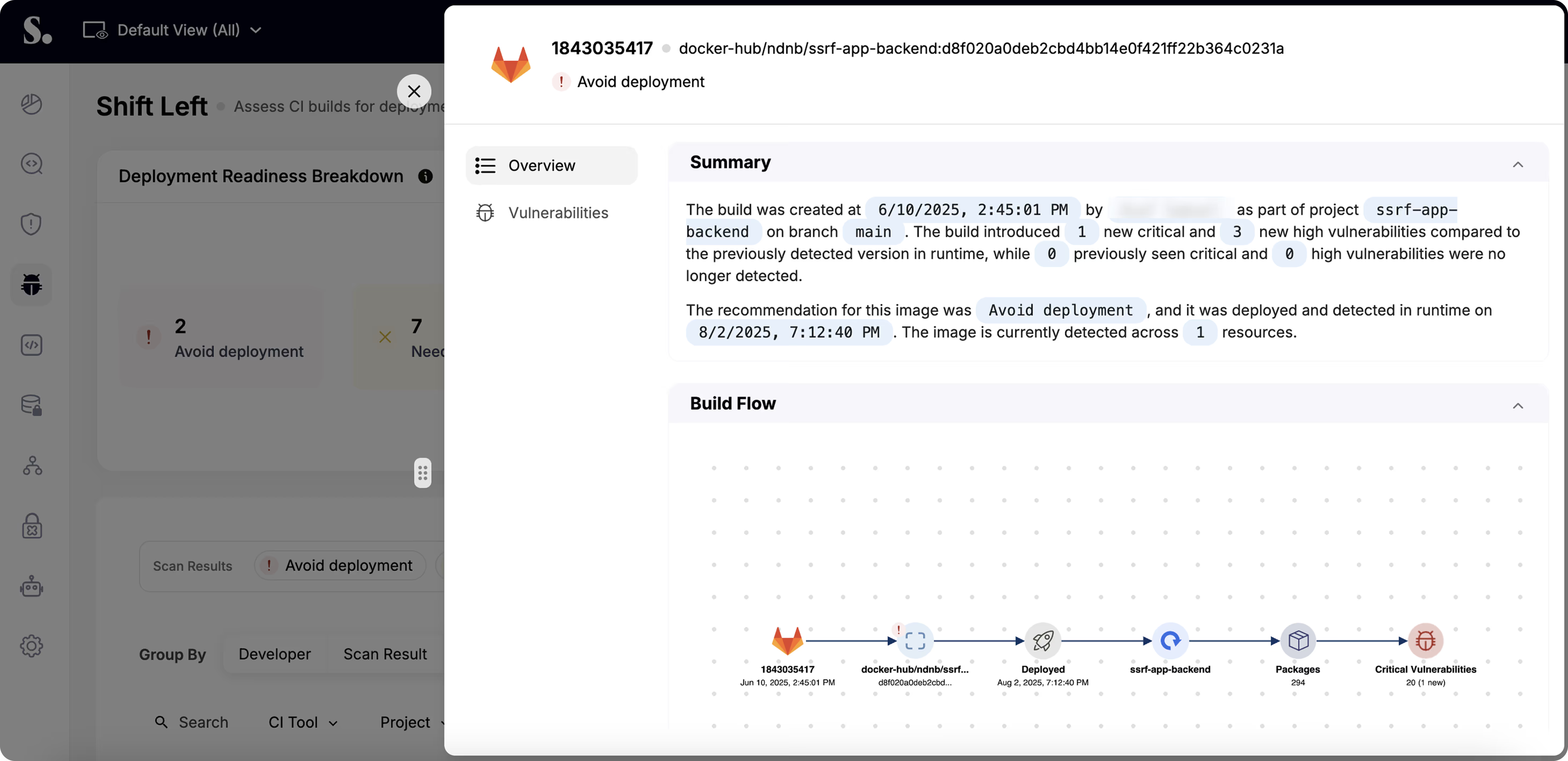
Stop risks before they reach production.
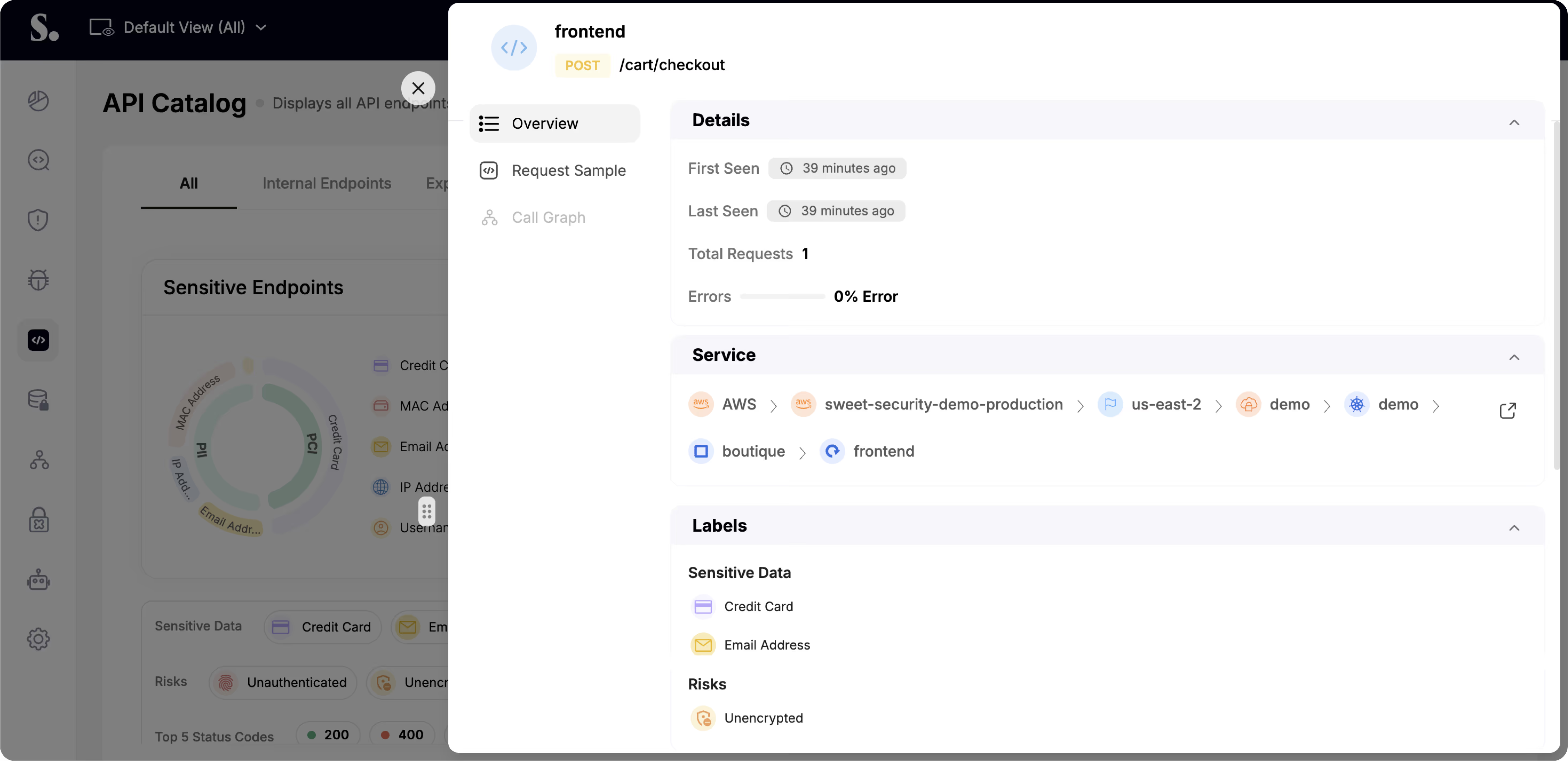
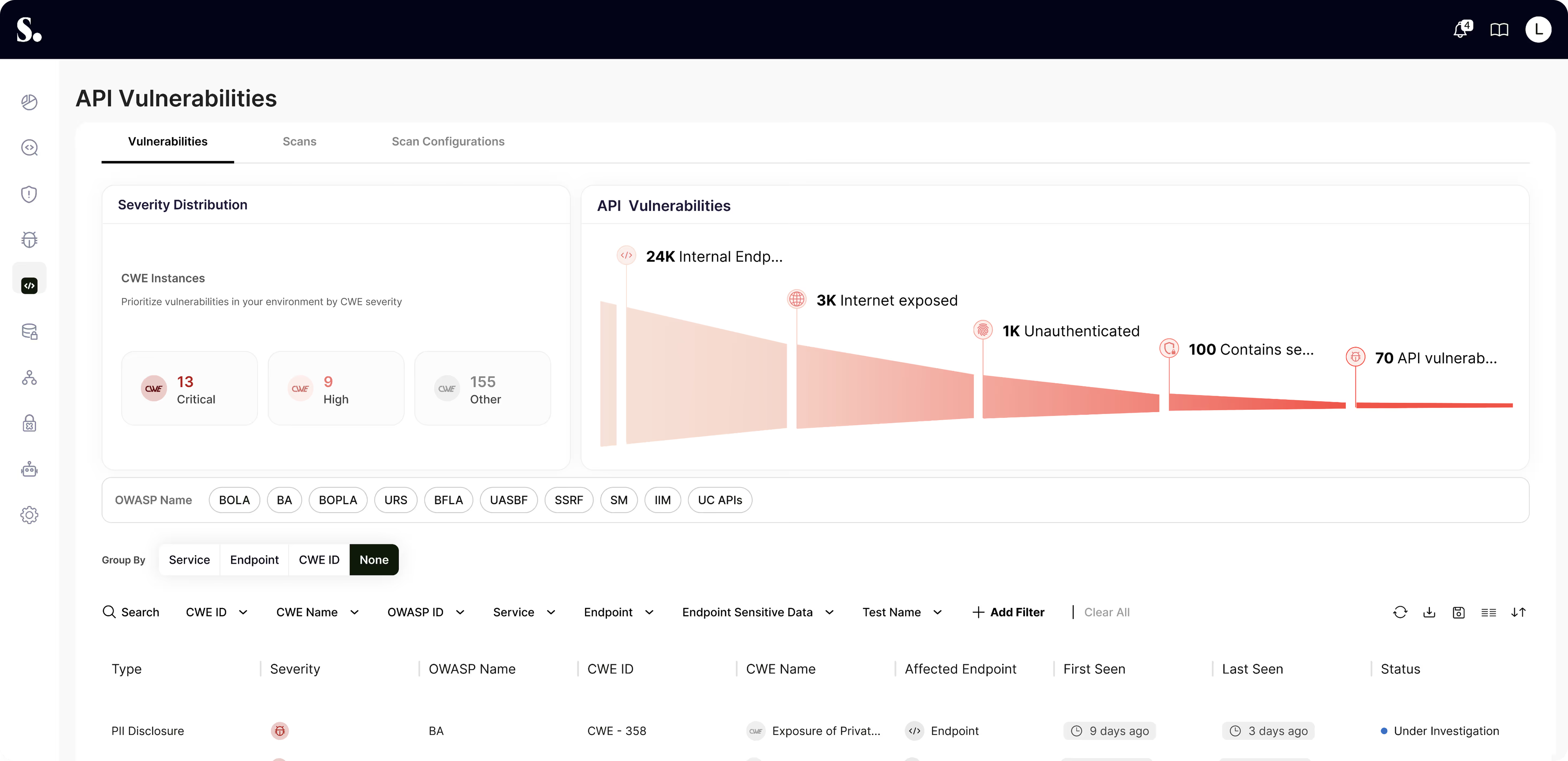
Gain the visibility and insight needed to protect against API threats and resolve them with confidence and speed.
See and manage data at rest (DSPM) and data in motion before it leaves your control.

Test live applications for exploitable weaknesses and identify vulnerabilities before attackers do.
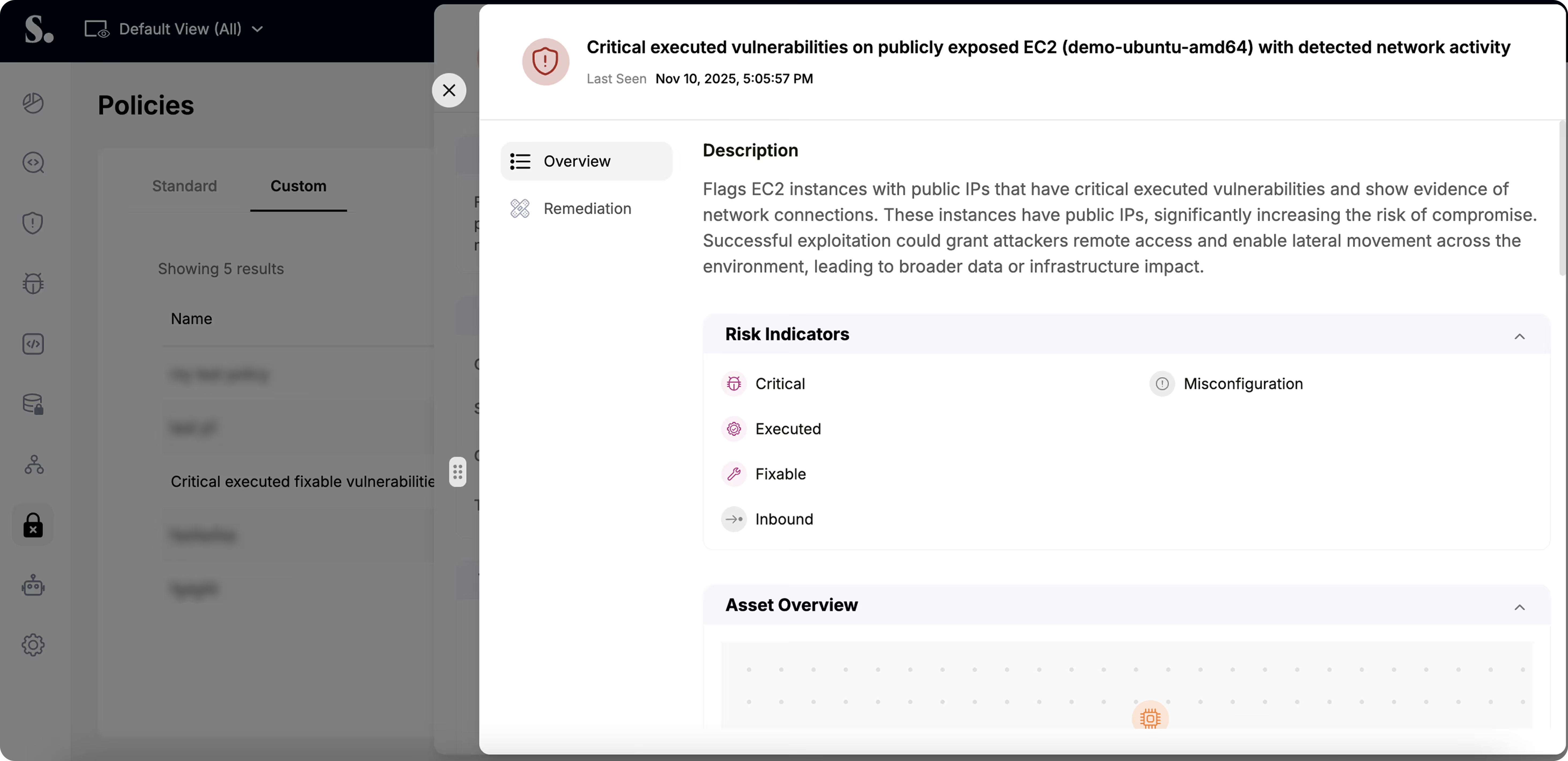
Manage real-time posture changes, remediate misconfigurations, and meet compliance standards with confidence.
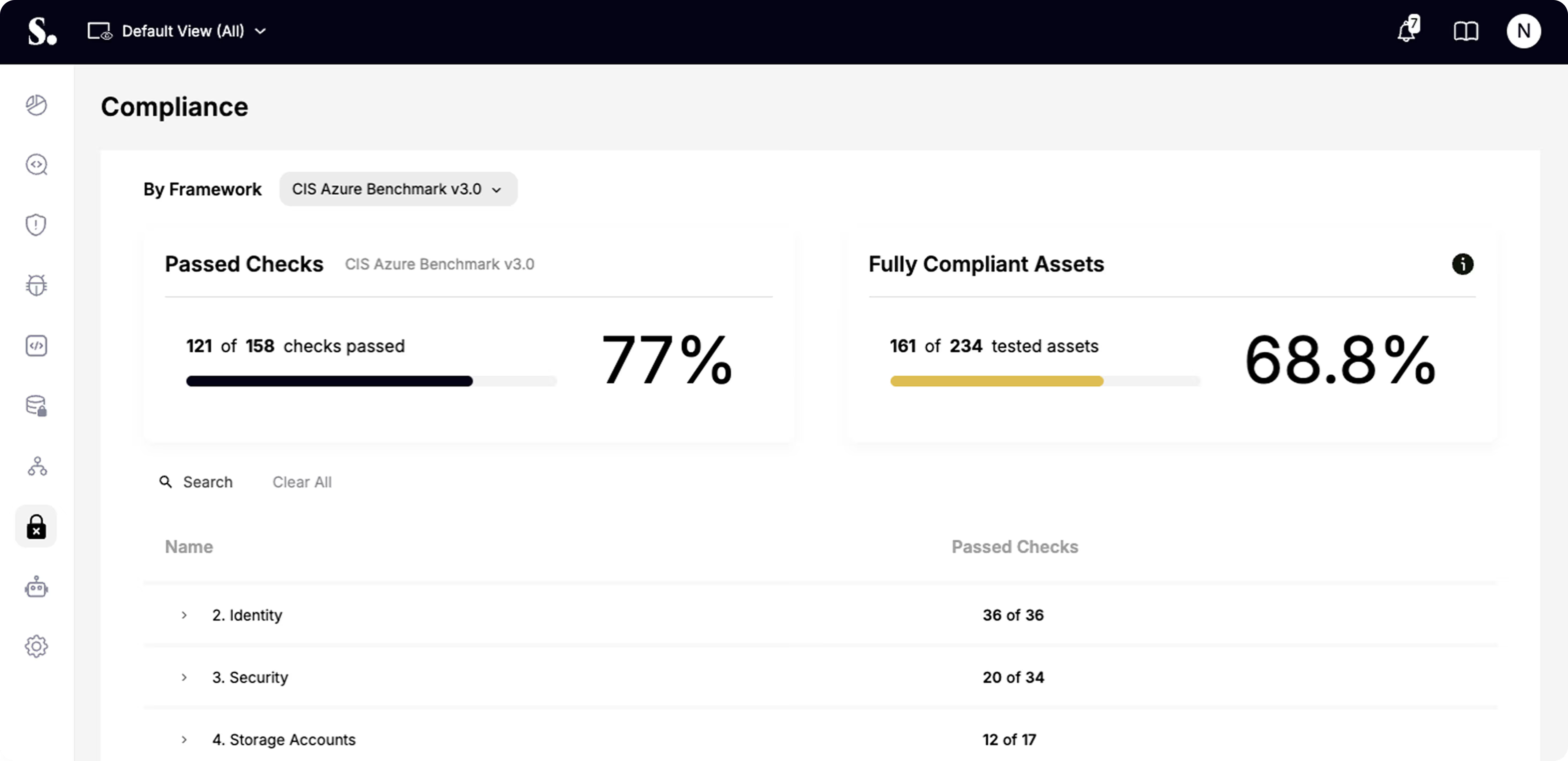
Conduct automated compliance checks against industry and custom frameworks.
Discover and map out your cloud environment in minutes.
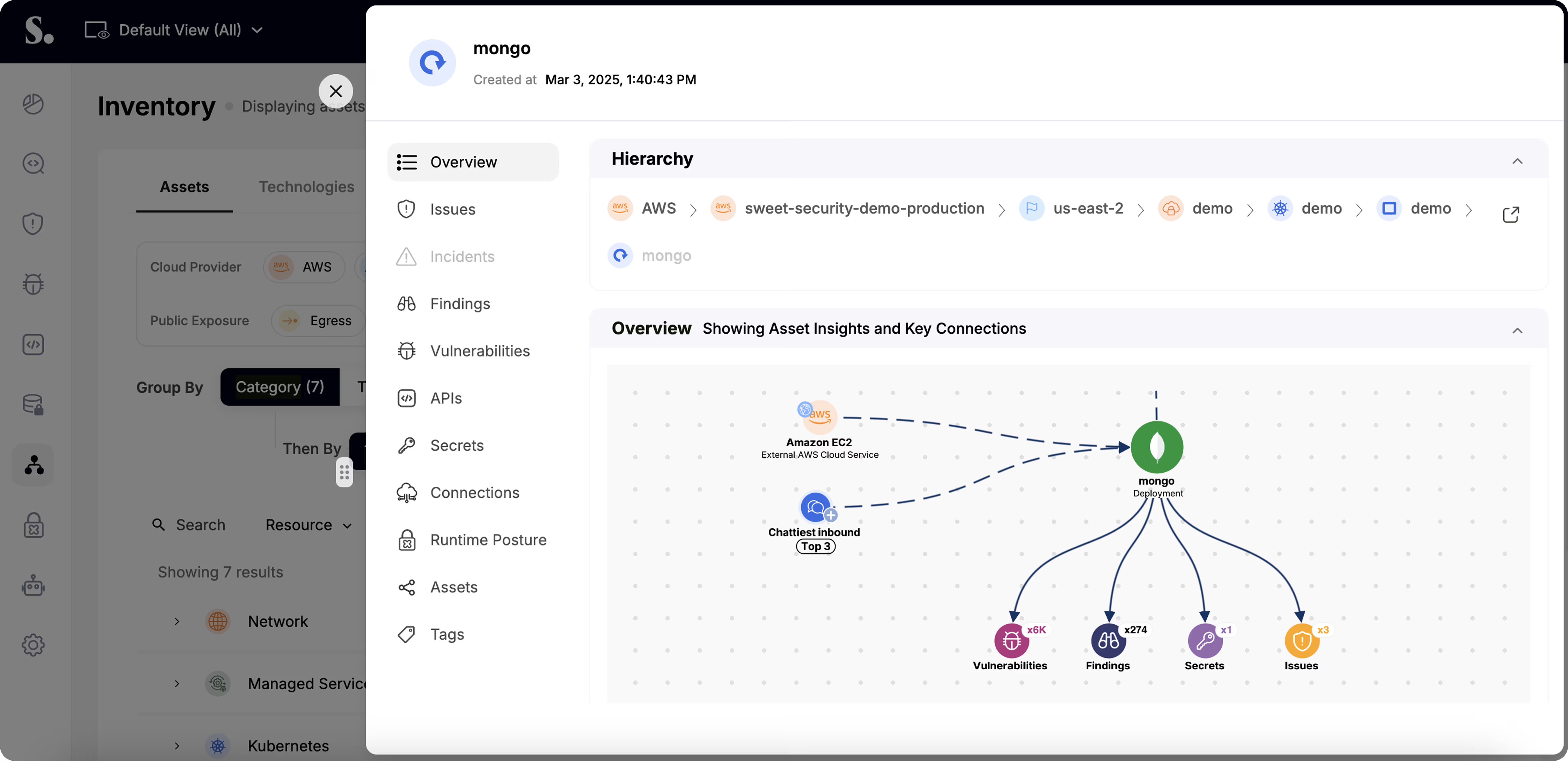
Gain a complete, contextual understanding of every workload in your environment.
Detect, prioritize, and remediate identity risks across your multi-cloud environment.