
You don’t need more alerts. You need to understand which ones matter — and why. Sweet Security gives SOC and Incident Response teams a complete picture of incidents across the cloud, workload, and application layers, with the context to act and the clarity to reduce MTTR across the board.




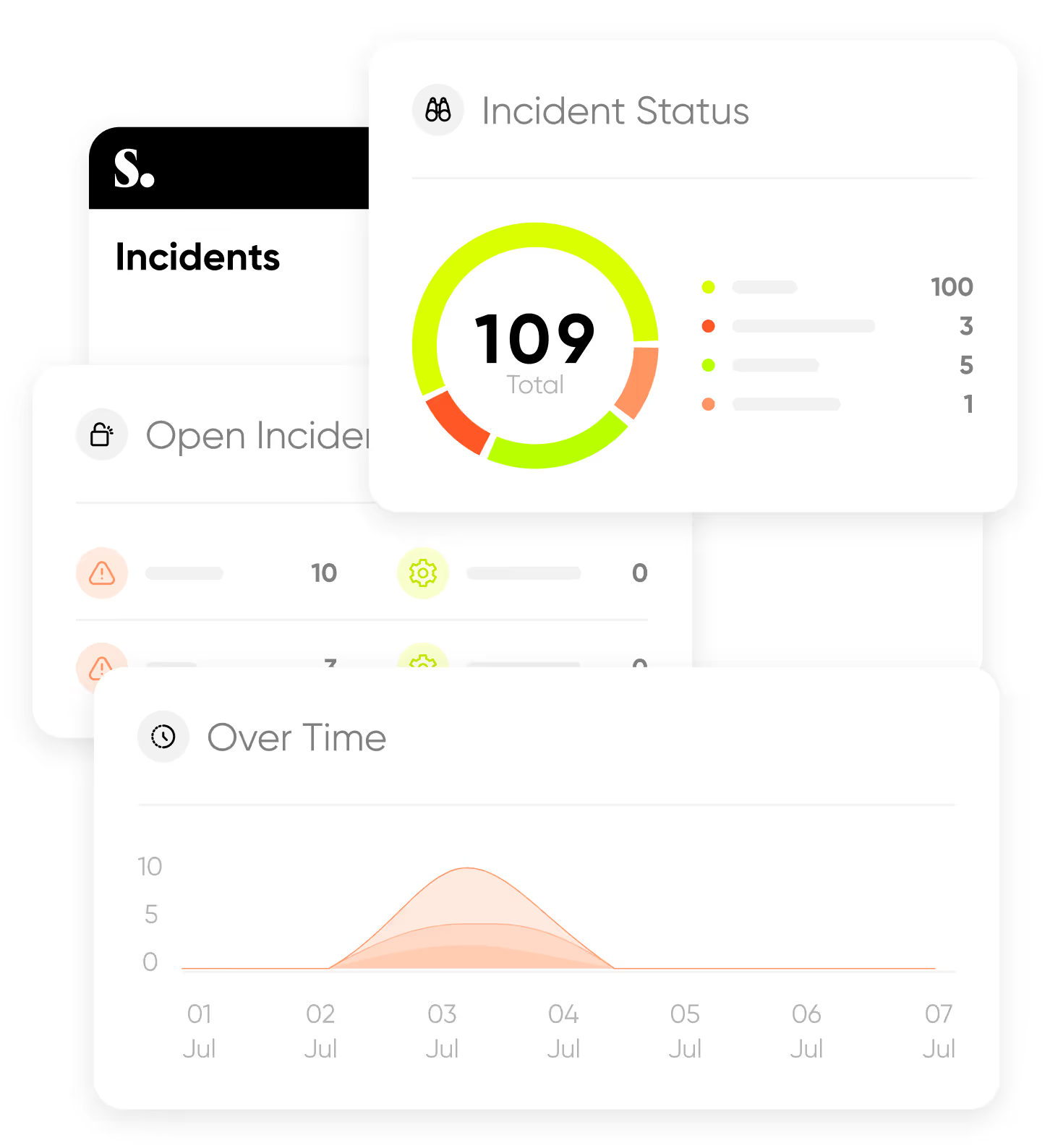
Sweet detects threats in real time, including zero-day exploits, misused identities, or known attack signatures. We monitor activity across:
Our engine correlates signals from every layer into a single incident, showing how an attacker moves across your environment — from initial access to lateral movement to the crown jewels.
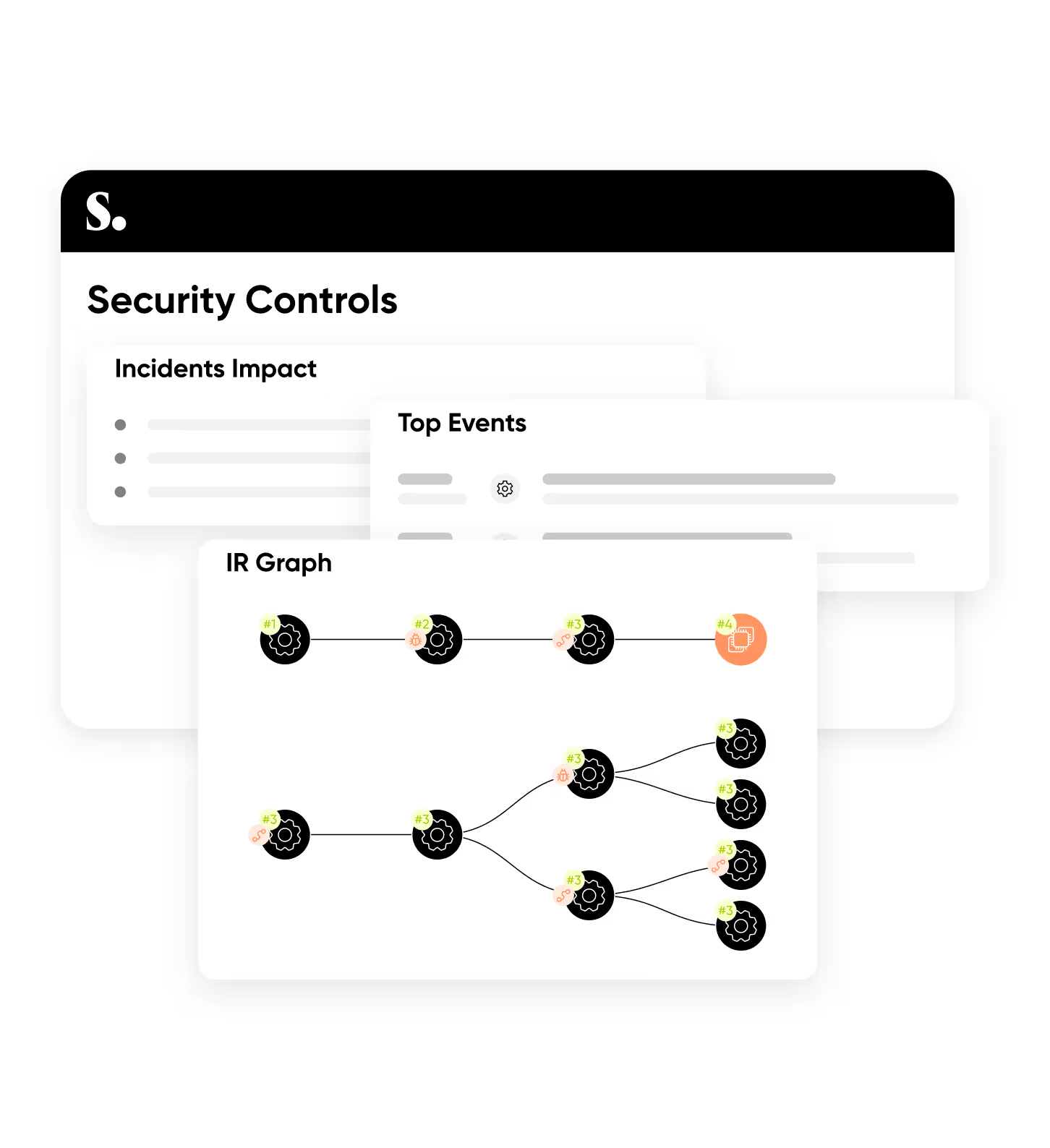
Detection is just the start. Sweet guides analysts through deep investigation:
Teams using Sweet reduce MTTR by over 90% — from hours to 2–5 minutes to fully understand and resolve incidents.
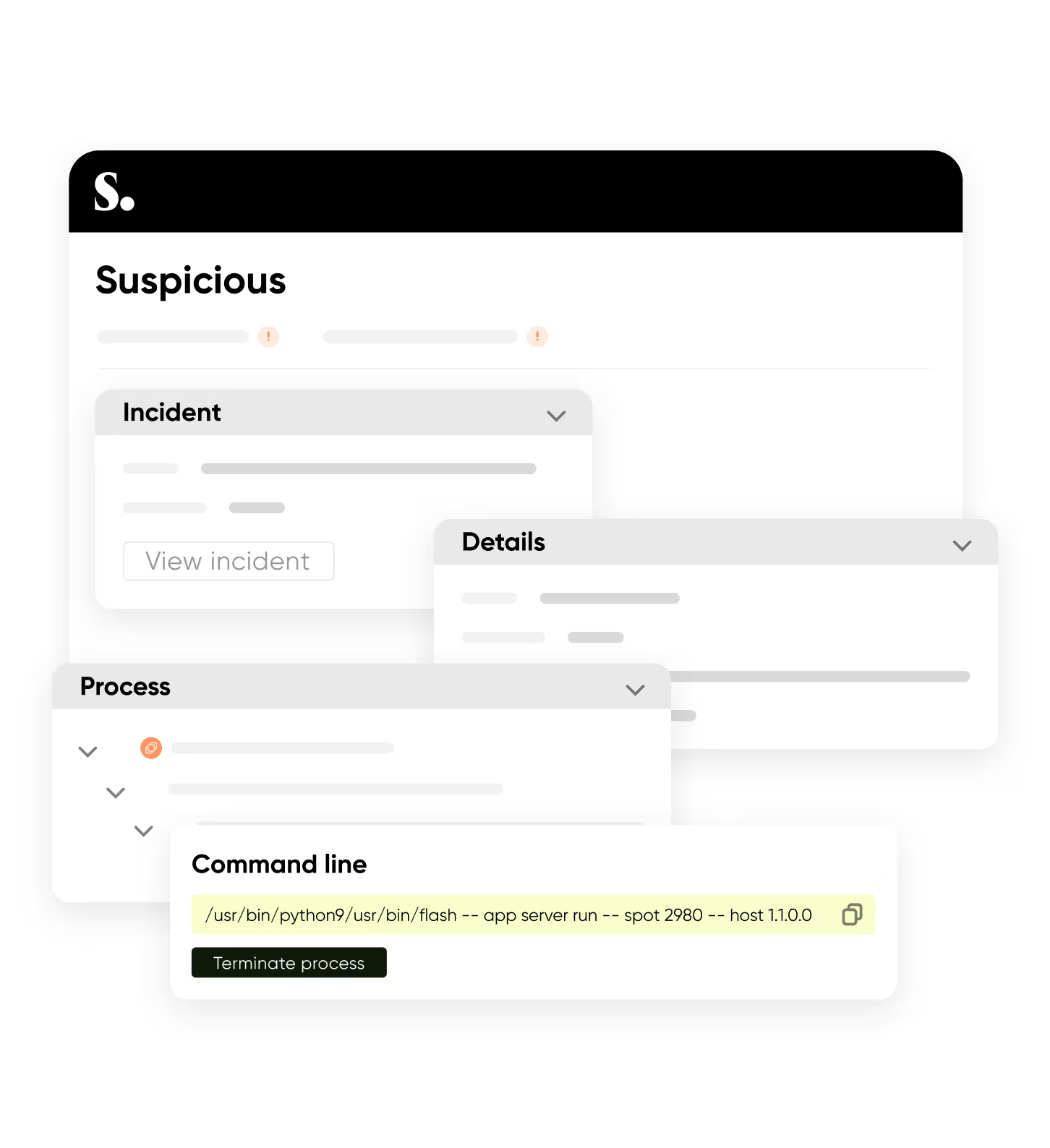
Once you've identified the threat, Sweet helps you shut it down:
Whether you respond manually or via automation, Sweet gives you the power to kick the attacker out in real time — not just alert on it.
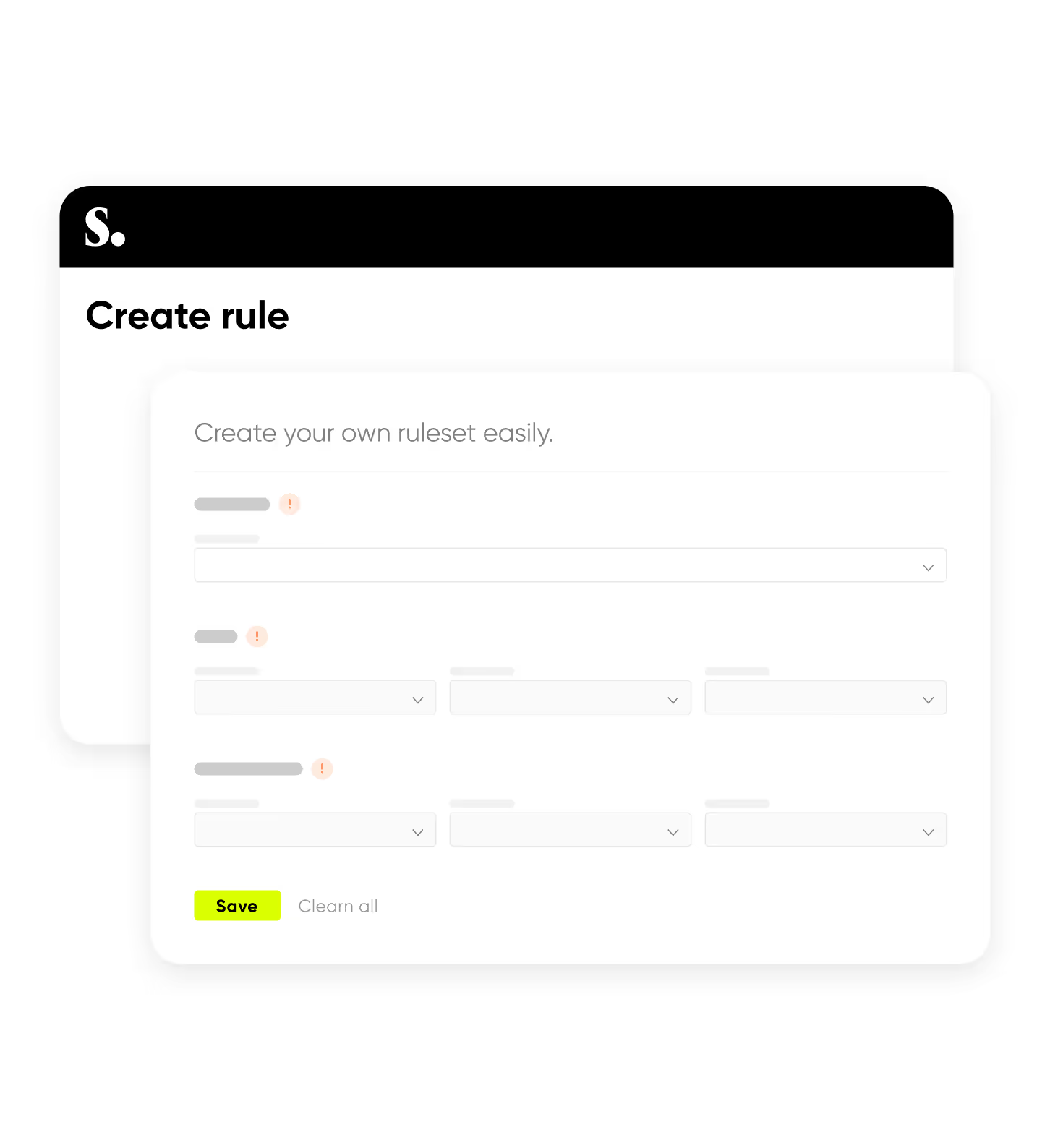
Every environment behaves differently. Sweet gives you the control to adapt:
It’s easy to create high-fidelity alerts for your environment, not just generic ones.
Sweet helps SOC teams reduce alert fatigue, investigate with confidence, and respond faster — without switching tools or stitching data together.
