Sweet Security is excited to share a major update: we've extended our runtime sensor to Windows environments! This means the same real-time visibility and detection capabilities that power Sweet’s Runtime CNAPP for Linux are now available for one of the most complex operating systems in enterprise cloud.
EDR Wasn’t Built for the Cloud
While Linux often dominates the cloud, many enterprise customers still rely heavily on Windows workloads, which come with their own unique set of security challenges. Windows environments inherently expose a larger attack surface compared to Linux, with specific components and system APIs like the registry requiring special attention. Often, security vendors simply repurpose their existing EDR agents (designed for laptops or PCs) for the cloud. However, these solutions weren't built for cloud-specific attack scenarios. Their reliance on rule engines and binary signatures falls short when benign tools can be abused for malicious purposes, allowing legitimate-looking binaries to slip past detection.
Sweet Security's sensor for Windows fundamentally changes this. Built from the ground up in Rust, it boasts a low resource footprint and high coverage. The sensor monitors everything from processes and files to network activity, and also addresses Windows-specific elements like registry manipulation, PowerShell scripting, DLL injection, and more. But the sensor goes even deeper and offers application-level traffic introspection, capturing Layer 7 data (requests and responses) to provide a complete understanding of application behavior.
We See it Different
What truly makes Sweet a game-changer is our renowned behavioral baselining. This advanced capability allows the sensor to identify legitimate tools being abused for malicious purposes, overcoming the limitations of signature-based detection. By understanding normal behavior, Sweet can accurately flag anomalies and threats that traditional solutions would miss, providing unparalleled protection for Windows cloud workloads.
Anomaly detection in the cloud is crucial since adversaries will usually hide their actions using existing tools. They call a benign binary, run a script, and use legitimate system utilities to do harmful things. If your sensor only records the top level, or looks for known signatures, you’re missing most of the picture.

As with all runtime signals, Sweet combines them with CDR (such as cloud audit logs) and ITDR (cloud identities, whether human or non-human) for full context and visibility in the decision-making process.
Real-World Detection: Sweet’s Windows Sensor in Action
To test the depth of Sweet’s new Windows runtime sensor, one customer conducted a joint evaluation that combined automated red-team exercises with realistic post-exploitation simulations. The goal was to measure detection across both MITRE-mapped and non-standard attacker behaviors.
Breakdown of the Attack
During the attack, a script was executed with an unrestricted policy, launching a chain of processes that ultimately ran:
C:\Windows\System32\reg.exe save HKLM\SAM C:\Windows\TEMP\sam
This command attempted to export the SAM (Security Accounts Manager) hive, where Windows stores password hashes, to a temporary file. It’s a classic credential-dumping maneuver often used in privilege-escalation and persistence stages.

What Sweet Saw
Within seconds, Sweet’s Windows sensor correlated a precise series of low-level events:
- PowerShell execution with unrestricted policy — flagged as a potential security risk.
- Registry export command — detected as an attempt to access and dump SAM data.
- File creation anomaly at C:\Windows\TEMP\sam — identified as sensitive data written to a non-standard location.
- Process lineage correlation — PowerShell → reg.exe relationship automatically reconstructed, giving full execution context.
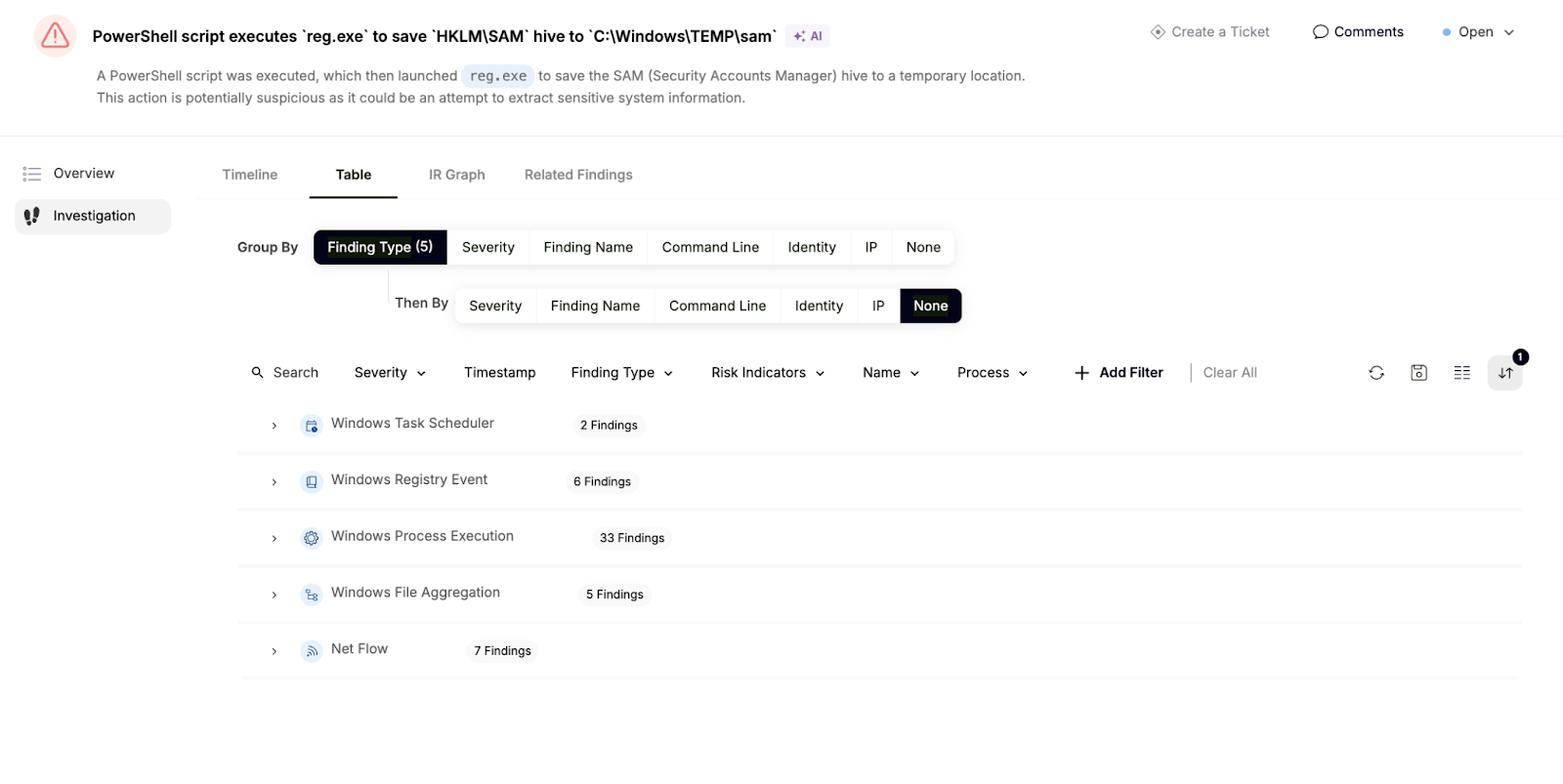
Sweet caught this attack not by looking at a single layer of the Windows OS, but by having visibility into multiple attack surfaces, including the Task Scheduler, the Registry, process execution, file operations, network flows and more.
The Investigation
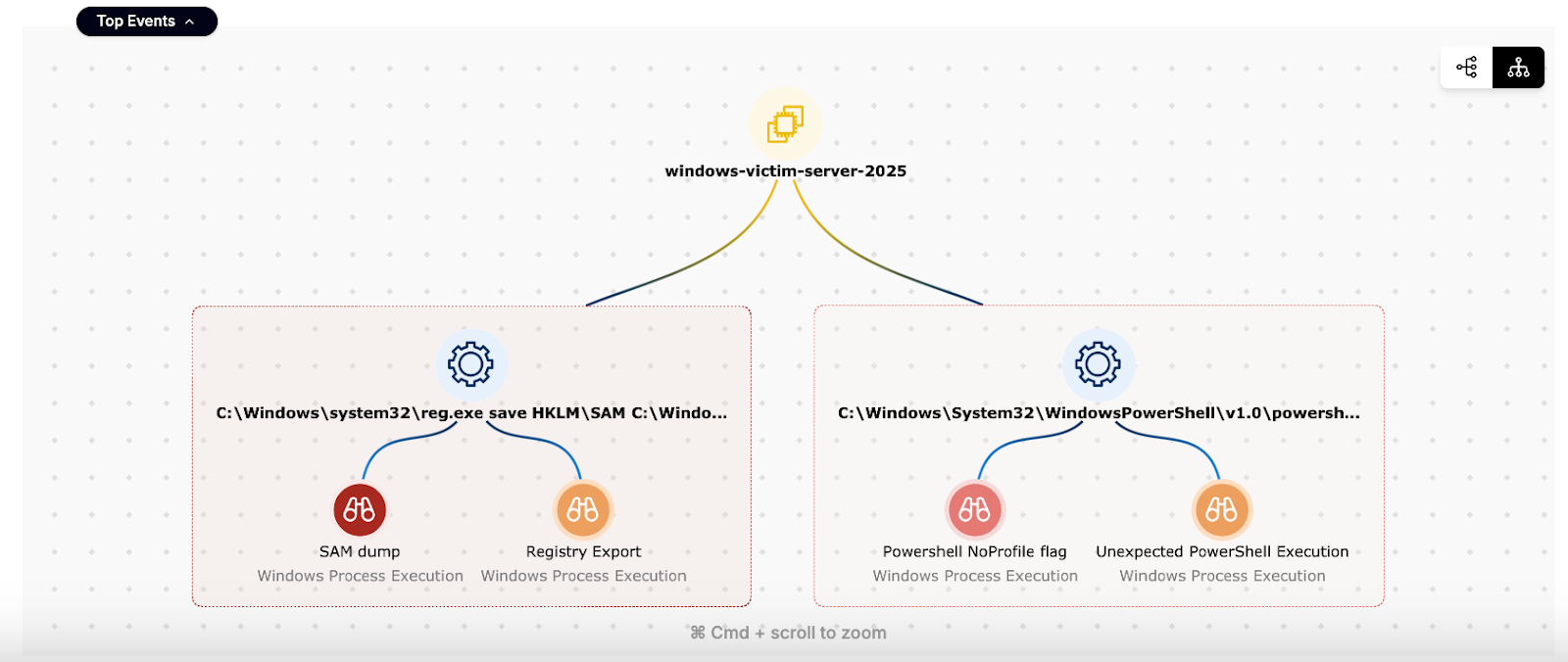
From the moment the attack began to the point of full investigation took less than two minutes. Sweet’s AI-driven investigation view automatically generated a narrative summary showing:
- Attack goal: Attempted credential extraction from the Windows SAM database.
- Affected assets: Windows instance within a production cloud account.
Potential impact: Exposure of password hashes and system credentials. - Visual Graph of the attack: Understanding how the attacker moved laterally within the environment.
Why It Matters
This scenario highlights why superficial process and file monitoring isn’t enough in Windows environments. Sweet’s runtime-native sensor doesn’t just record system calls, it understands system behavior, correlates events and detects anomalies. This allows Sweet to detect both known and unknown techniques, including those used in real-world multi-stage attacks like this one.

The Power of Sweet’s Runtime CNAPP for Windows
Extending runtime coverage to Windows completes Sweet’s vision for full-stack protection. Whether workloads run on Linux or Windows, Sweet’s CNAPP now delivers:
- Deep telemetry across process, file, registry, DLLs and more
- Behavioral baselines for anomaly detection
- LLM-powered correlation and investigation that transforms raw events into human-readable context
- Identity and source information, which makes it easy to immediately understand which identities and cloud resources were compromised
With this launch, Sweet Security provides runtime-native protection for every cloud, closing one of the industry’s most persistent visibility gaps. For more information on Sweet’s Window sensor or Runtime CNAPP, book a demo today or contact your customer support representative.




%20(1).png)






