Cloud-native development moves fast. Code is built, shipped, and deployed into production in minutes, and vulnerabilities can move just as quickly.
Most security teams try to manage risks in silos. Developers scan during CI, security checks registries on a schedule, and operations monitor runtime. The problem? That fragmented view leaves gaps.
At Sweet, we built a 360° vulnerability management framework to fix that, delivering continuous protection across the entire application lifecycle, from the moment code is written to the workloads running in production.
Here’s how we help teams secure every stage of the journey.
1. Shift Left: Prevent Vulnerabilities Before They Deploy
Security should start early, but it should also be informed.
Our platform integrates directly into your CI/CD pipelines, scanning images at build time to detect vulnerabilities before deployment. Developers get real-time, actionable guidance without leaving their workflow.
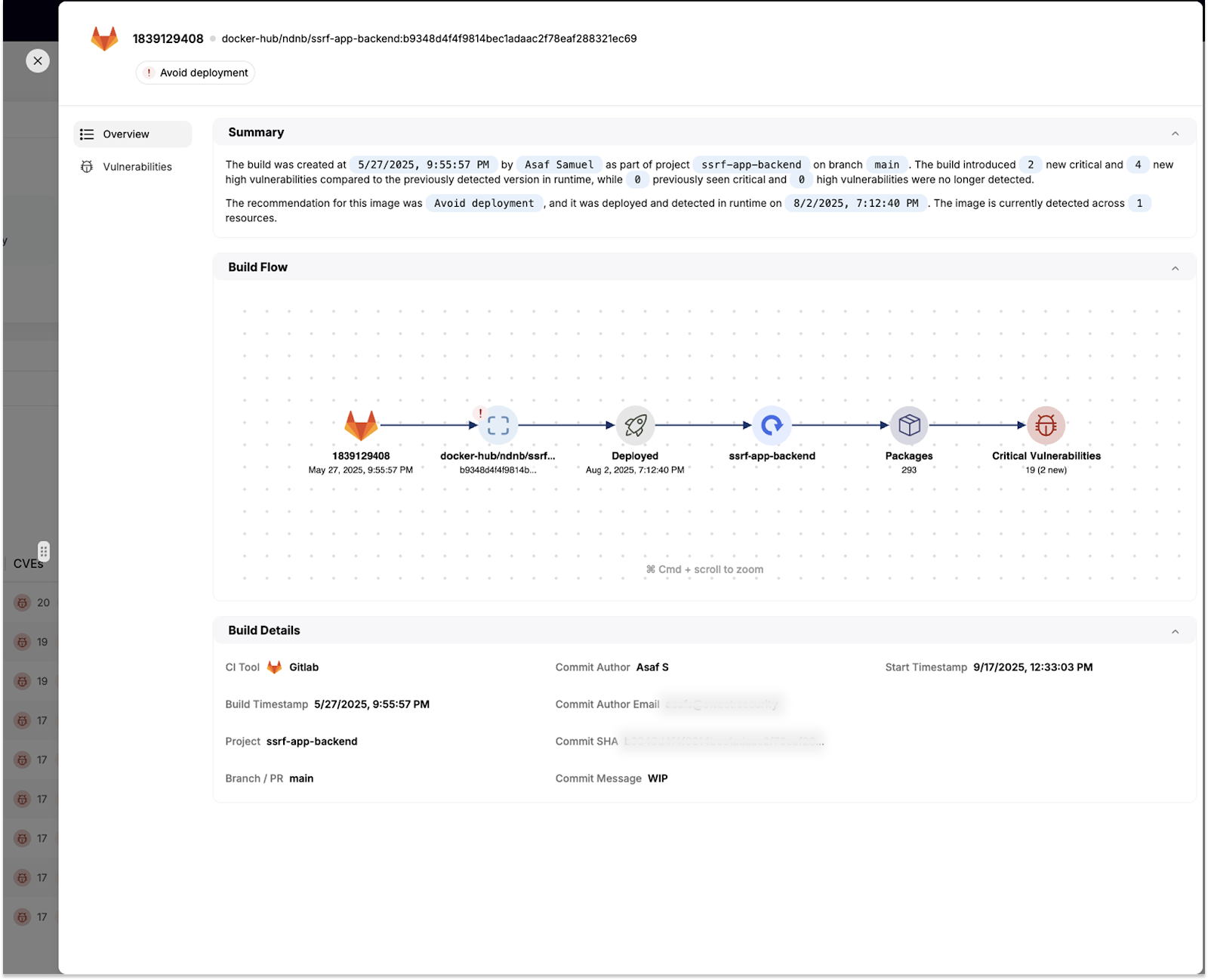
But we don’t just flag issues, we help teams make context-aware deployment decisions. By enriching build-time scans with runtime intelligence, our system knows how workloads behave once deployed, which components are executed, exposed, or critical.
That context allows us to provide specific recommendations on whether an image should be:
- Blocked from deployment,
- Deployed with caution, or
- Approved as safe to proceed.
This helps security and DevOps teams find the right balance between safety and agility, stopping high-risk deployments without creating unnecessary friction.
Key benefits:
- CI/CD integration for early, automated detection.
- Runtime-enriched context for smarter decisions.
- Clear deployment recommendations, not just scan results.
2. Registry Scanning: Securing Images at Rest
Even with strong shift-left practices, risk evolves. New vulnerabilities emerge daily, and previously safe images can become exposure points overnight.
Our Sweet Registry Scanner provides continuous visibility and assurance across your registries (AWS ECR, Docker Hub, GCP Artifact Registry, and others) scanning all stored images for vulnerabilities and configuration risks.
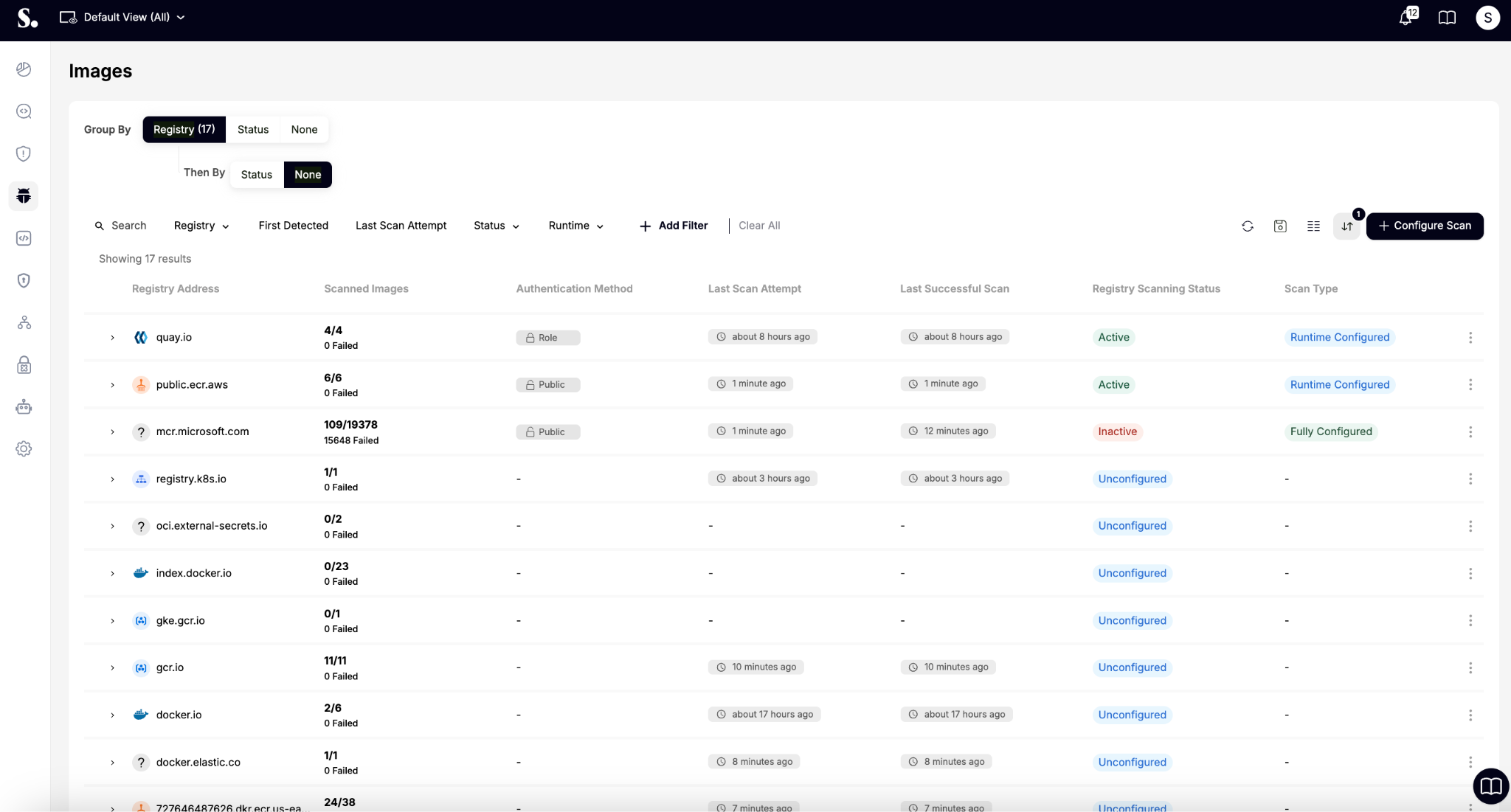
The Registry Scanner goes beyond one-time checks:
- Continuous scanning and automatic rescans as new CVEs are disclosed.
- Registry health and authentication monitoring, so you always know connection status.
- Cross-correlation with runtime, identifying which vulnerable images are actually active.
- Configurable scan types, from full registry coverage to targeted rule-based scans.
This capability bridges prevention and detection, protecting your environment earlier in the image lifecycle while complementing runtime-based discovery.
3. Runtime Vulnerability Catalog: Focus on What Really Matters
Once your workloads are running, the question changes from “What’s vulnerable?” to “What’s truly at risk?”
Our Runtime Vulnerability Catalog gives you that answer. It enriches every CVE with runtime context, tracking which packages are actually executed, loaded into memory, or exposed via inbound connections.
Then, we take prioritization a step further with the Sweet Score - a dynamic, context-aware scoring model that replaces static CVSS ratings with a more accurate measure of real-world risk.
Sweet Score combines:
- Runtime activity (executed vs. dormant code)
- Exposure signals (open ports, inbound connections, network paths)
- Workload context (asset sensitivity and service importance)
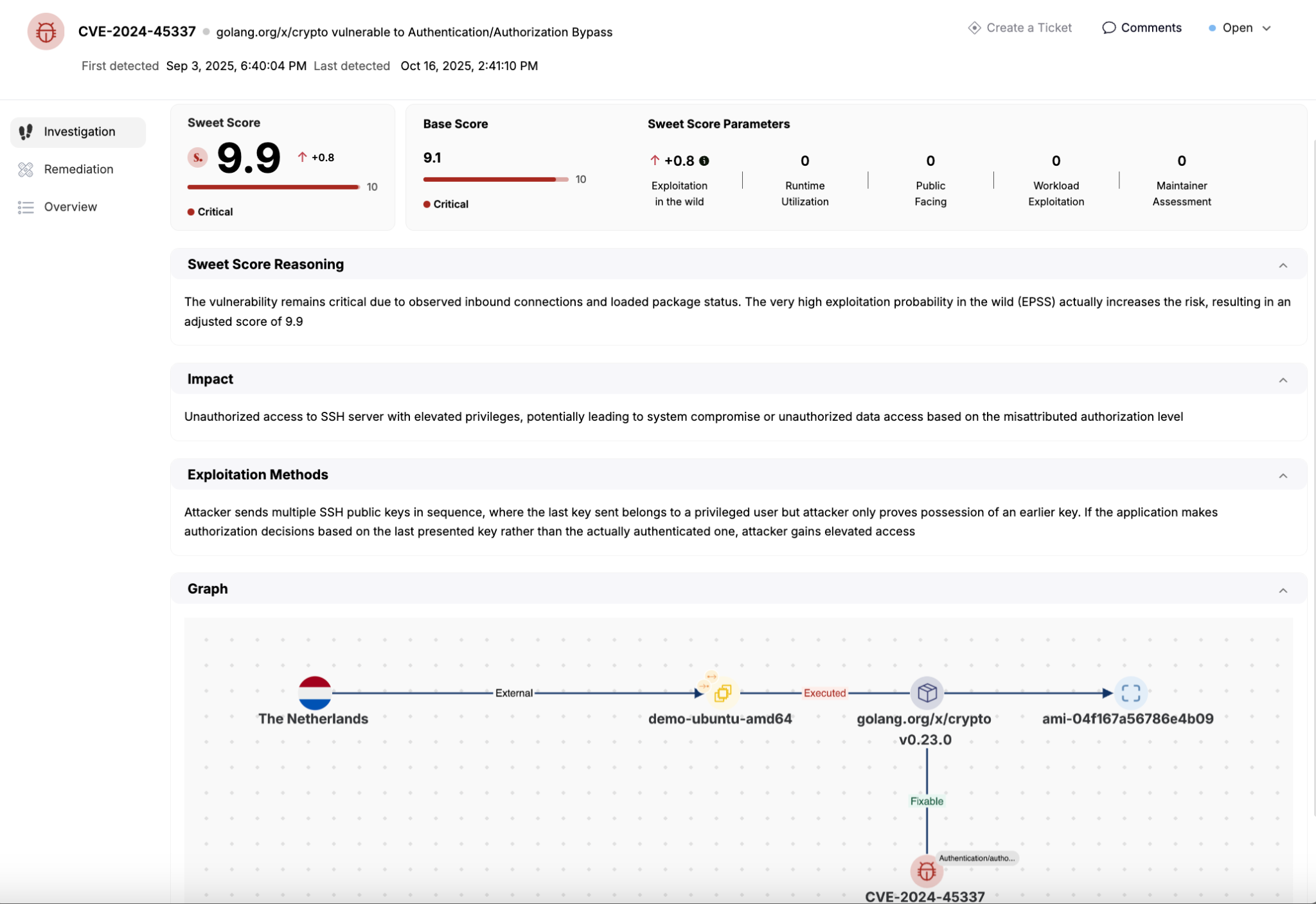
The result? A vulnerability prioritization system tailored to your actual environment. Your teams can focus on fixing what’s exploitable, not on chasing what’s irrelevant.
A Continuous Lifecycle of Security
Bringing these three pillars together, Shift Left, Registry Scanning, and Runtime Intelligence, creates a continuous feedback loop of protection.
- Developers secure what they build.
- Security teams maintain complete visibility across registries.
- Operations focus on what’s truly risky in production.
That’s the essence of modern CNAPP-driven vulnerability management: connected, contextual, and continuous. Our platform doesn’t just find vulnerabilities; it understands them in context, prioritizes them based on real exposure, and helps you eliminate them faster. From code to cloud, you gain the visibility and confidence to move at the speed of innovation, securely.
Ready to See It in Action?
Get a demo of how our 360 degree vulnerability management gives your team complete coverage from build pipelines to runtime with real-time visibility, Sweet Score prioritization, and continuous protection.

.jpg)









