When it comes to securing modern applications, speed and safety often feel at odds. Developers want to ship quickly, while security teams need assurance that code and infrastructure are safe to run. That’s why Sweet has extended its security coverage further left in the development process—directly into CI builds—so risks are caught before they ever make it into production.
Shifting Security Into the CI Build
Our new integration works seamlessly with multiple CI tools (like GitLab, GitHub, and others), embedding vulnerability analysis directly into the build process. Each build is automatically scanned, and before any deployment takes place, we assess:
- New vulnerabilities introduced since the last build
- Severity of those vulnerabilities
- Runtime context of where the image is likely to run (based on previously observed runtime tags)
This means that deployment recommendations are no longer just theoretical. Instead, they’re grounded in both vulnerability data and the runtime signals of the environment where the build is headed.
From Build to Decision: Deploy or Hold Back
Every build that passes through the pipeline gets a clear recommendation from Sweet, making it easy for both developers and security teams to decide on next steps:
- Ready to deploy: The build introduces no new material risks compared to what’s already running in production. You can ship it with confidence, knowing that it doesn’t expand your attack surface.
- Needs review: The build contains changes worth looking at but not necessarily blocking. For example, it may include non-critical vulnerabilities that weren’t present in the currently deployed image. These differences don’t always translate to an immediate risk, but they do warrant a closer look before deployment.
- Avoid deployment: The build carries risks that make deployment unsafe. This could mean critical vulnerabilities with known exploits in the wild, services exposed to relevant inbound connections, or runtime-sensitive weaknesses that could be targeted if pushed live. In short: if attackers could realistically use these vulnerabilities against your environment, we flag the build to stop it before it reaches production.
As shown in the screenshot below, deployment readiness is broken down at a glance. Builds that introduce dangerous vulnerabilities are flagged before they can move forward, ensuring teams avoid preventable incidents.
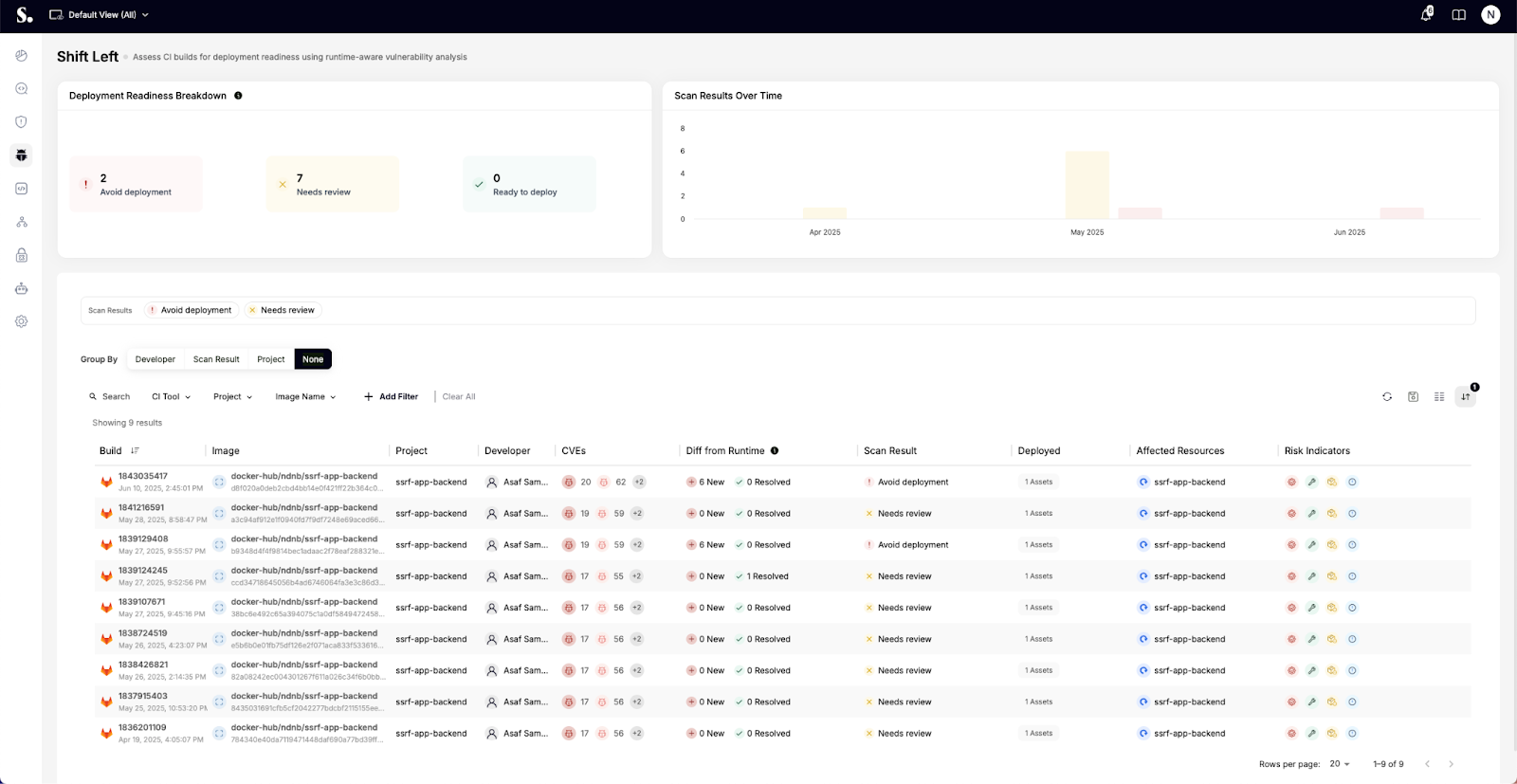
Developers also get visibility into which vulnerabilities were introduced, how they compare to the runtime version, and what resources would be impacted if the build goes live.
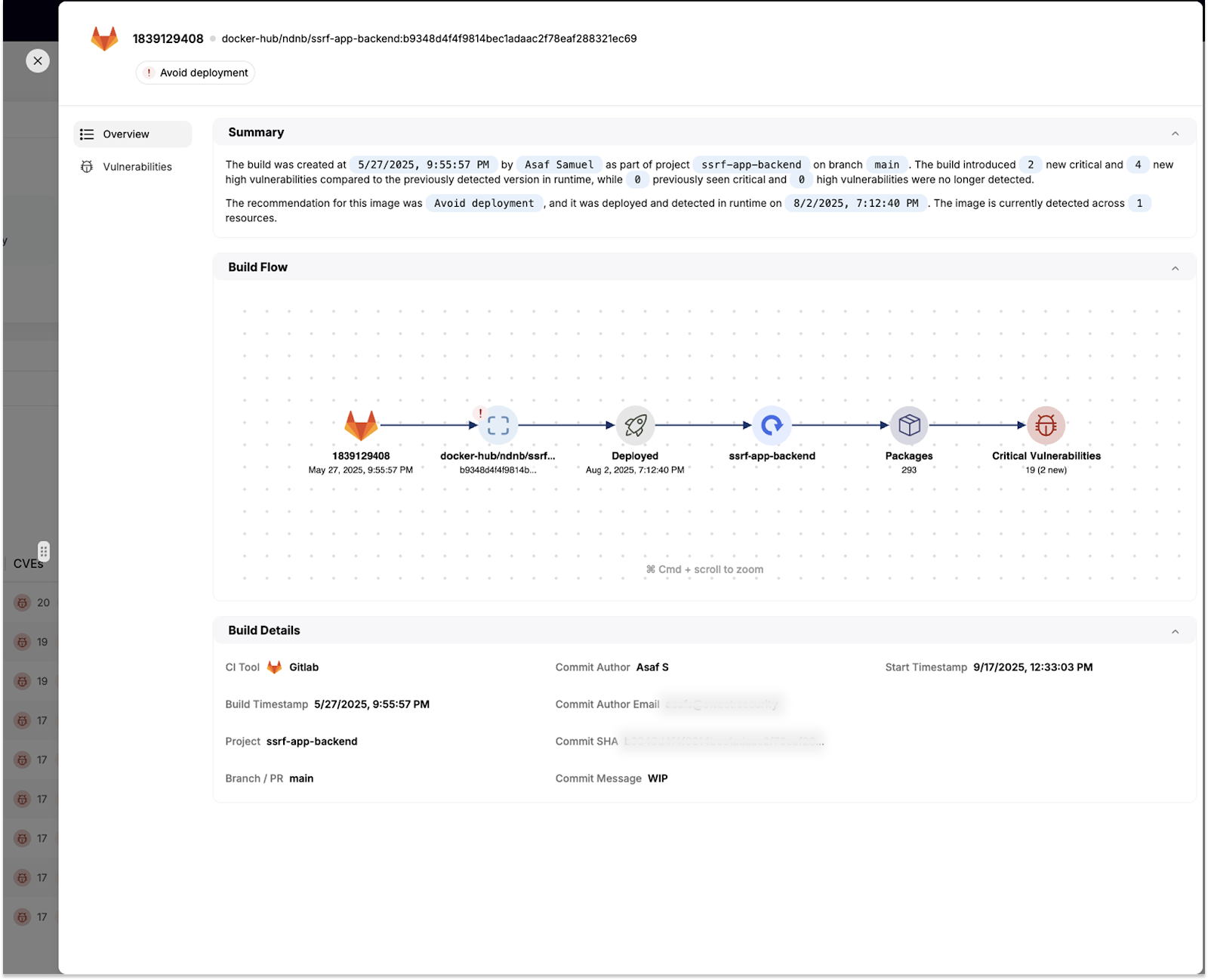
Completing the Vulnerability Picture
This CI/CD integration doesn’t live in isolation—it’s part of a broader vulnerability detection strategy. By combining:
- Runtime vulnerability catalog: Continuous detection and prioritization of vulnerabilities in running workloads
- Container registry scanning: Ensuring images are safe before they’re pulled
- Pre-deployment CI build scanning: Catching risks before deployment decisions are made
You get a full-spectrum view of vulnerabilities across the entire software lifecycle.
Why It Matters
This approach turns deployment security from a reactive process into a proactive safeguard. Developers no longer have to wait until runtime alerts surface to learn about issues. Instead, the system makes informed, context-aware recommendations at the moment they matter most—before deployment.
The result is faster, safer shipping with fewer production headaches and a stronger security posture across the board.
To learn more about Sweet’s shift left capabilities, book a demo today or contact your customer support representative to learn more.

.jpg)


.png)






