In modern cloud-native environments, sensitive data moves between workloads, services, and endpoints. Yet most organizations lack a clear answer to a fundamental question:
Where is the sensitive data in my environment going and how is it being transmitted?
The problem isn’t just about detecting sensitive data once. It’s about knowing when that data is moving to the wrong places, like unencrypted endpoints, external services, or workloads that were never supposed to process it in the first place.
Without that visibility, blind spots form. Blind spots that can lead to data leaks, compliance violations, and unnecessary business risk.
The Importance of Securing Data in Motion
Security and compliance teams need to know more than just whether sensitive data exists. They need context:
- Which workloads and endpoints are transmitting it?
- Is sensitive data leaving the organization?
- When did it first appear in this workload, and has it been seen before?
- How many requests contain that data, and what’s the pattern over time?
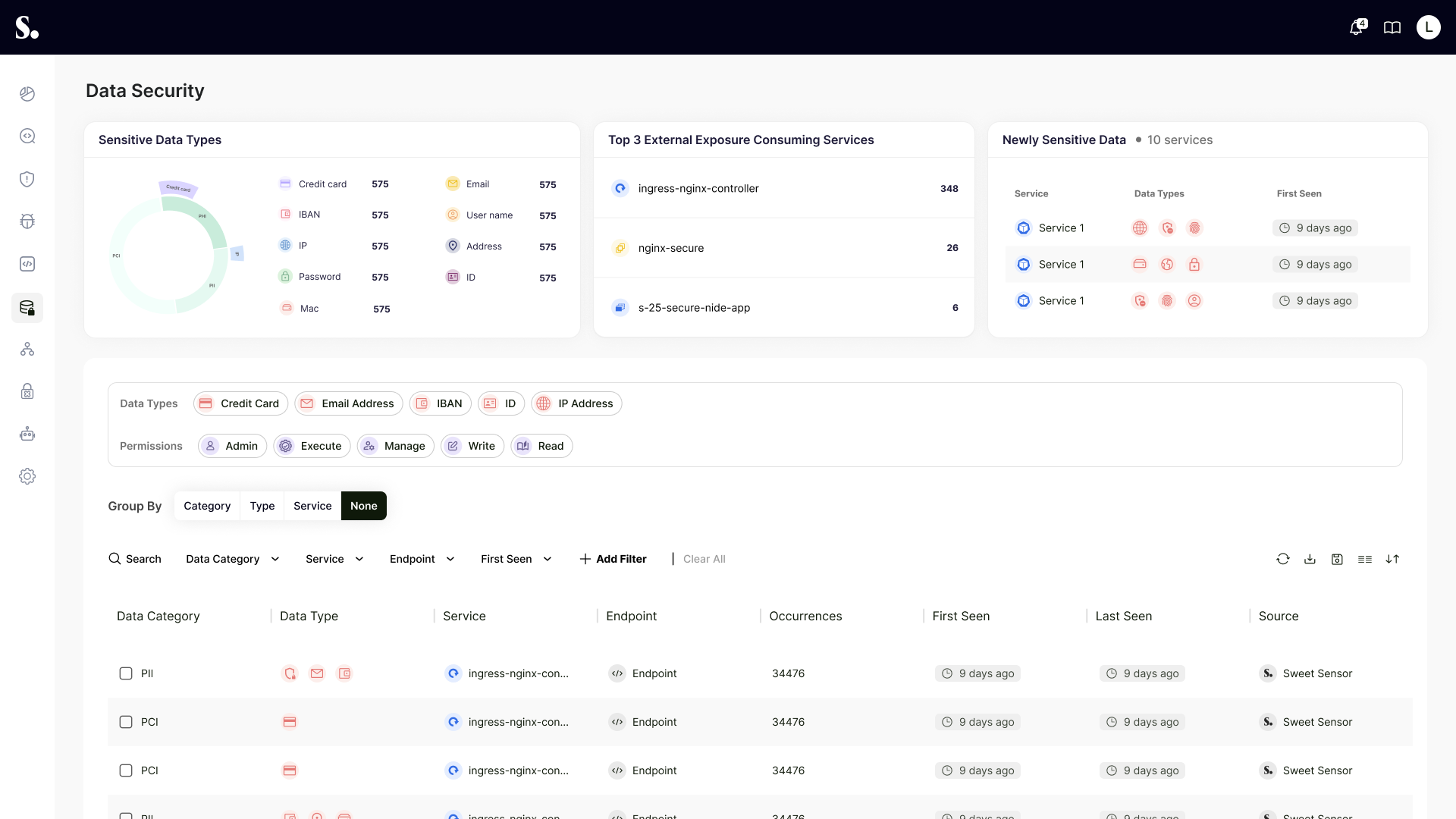
At Sweet Security, we believe data protection starts with clear, contextual visibility. That’s why we’re introducing Data Security at Sweet — a centralized place for all sensitive data detections across your organization.
Instead of scattered findings, you get one place to:
- See every sensitive data type detected (PII, PCI, PHI, secrets)
- Understand where that data is moving — by service, endpoint, and request
- Spot risky data egress to external endpoints
- Track when sensitive data is seen in a workload for the first time
- Investigate faster with direct drill-down into endpoint-level context
Key Capabilities
1. Sensitive Data Inventory & Classification
A comprehensive list of all sensitive data types detected in your environment. Each entry shows:
- Data category (PII, PCI, PHI)
- Data type (email address, credit card, password, IP address, etc.)
- Service and location (endpoint)
- Number of requests containing sensitive data
- First seen / last seen timestamps
- Detection source (Sensor, with ZAP scans and others to follow)
2. Sensitive Data Egress
Not all sensitive data is equal and not all traffic is safe. The Sensitive Data Egress widget highlights requests where sensitive data was transmitted to external domains or IPs. This visibility makes it possible to spot data leaving the organization, often the most urgent form of exposure.
3. Newly Detected Sensitive Data
The New Workloads with Sensitive Data widget surfaces workloads where sensitive data was seen for the first time in the past 24 hours. This helps teams immediately identify new risks caused by code changes, integrations, or service misconfigurations.
4. Data Mapping
Trace how sensitive data flows across your environment. Map endpoints, services, and access paths so you can understand which workloads interact with critical assets and where potential exposure points exist.
5. Data Compliance
Check your environment continuously against industry and regulatory benchmarks. With built-in validation, you can prove compliance at any time and reduce audit fatigue.
6. AI Data Security
Monitor and control sensitive data sent to third-party AI services. Sweet detects when payloads include PII, PCI, or PHI—even if requests are authenticated—so you can prevent unintentional leaks to AI tools.
7. Data Loss Prevention (DLP)
Block or flag authorized or unauthorized transfers of sensitive data outside your environment. Whether accidental sharing or a malicious attempt, Sweet provides the visibility needed to stop it before damage occurs.
8. Encryption & Authentication Verification
Ensure every sensitive data flow is protected in transit. Sweet verifies encryption and authentication across workloads and flags unprotected or misconfigured transmissions that could lead to breaches.
9. Powerful Filtering and Grouping
Drill down by data category, type, service, or endpoint. Group findings to match your investigation workflow, and with every entry linked to the endpoint drawer, you can pivot seamlessly from overview to detail.
Real Customer Use Case: Detecting DLP to Third Party AI Services
One of our customers in the manufacturing sector uses OpenAI services like ChatGPT to streamline development. Sweet detected that sensitive data was unintentionally included in a payload sent to OpenAI. The request was authenticated and legitimate, but the data—containing PII—should never have left the environment.
Sweet flagged the event immediately, showing the customer exactly what was transmitted and where. This wasn’t a malicious act, but a simple mistake that could have resulted in exposure if left unnoticed. By providing visibility into sensitive data in motion, Sweet helped the customer quickly contain the issue, prevent future leaks, and ensure sensitive information stays protected—even when interacting with trusted AI services.
The Future of Data Security, Backed by Runtime
Sensitive data is moving faster and wider than ever before. The challenge isn’t just detection; it’s understanding how that data flows across your environment and where it’s at risk.
Data Security at Sweet gives security, compliance, and engineering teams the context they need to eliminate blind spots, reduce exposure, and strengthen compliance. It’s time to see sensitive data clearly and act on it confidently.











